Search for "Tom Wills" returned 4682 results

59 min
An Overview of Secure Name Resolution
DNSSEC, DNSCurve and Namecoin

92 min
Was tun, wenn Tod?
Let's talk about death, baby
38 min
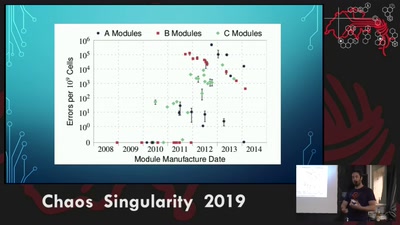
Rowhammer exploit
Viability of the Rowhammer Attack when ECC memory is used

16 min
Production-Ready Virtualisation with Harvester and Longhorn
Harvester in Prod
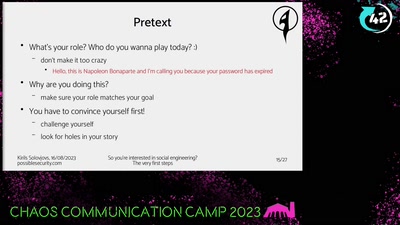
44 min
So you're interested in social engineering?
The very first steps

61 min
Untrusting the CPU
A proposal for secure computing in an age where we cannot…

46 min