The 37th Chaos Communication Congress (37C3) takes place in Hamburg, 27.-30.12.2023, and is the 2023 edition of the annual four-day conference on technology, society and utopia organised by the Chaos Computer Club (CCC) and volunteers.
Congress offers lectures and workshops and various events on a multitude of topics including (but not limited to) information technology and generally a critical-creative attitude towards technology and the discussion about the effects of technological advances on society.
58 min
Operation Triangulation
What You Get When Attack iPhones of Researchers

41 min
Back in the Driver's Seat
Recovering Critical Data from Tesla Autopilot Using Voltage…

46 min
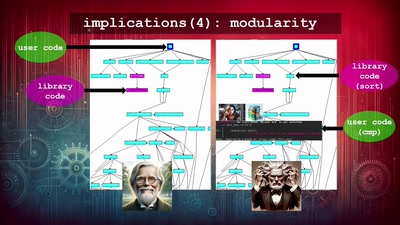
Writing secure software
using my blog as example

63 min
All cops are broadcasting
TETRA unlocked after decades in the shadows

41 min
Why Railway Is Safe But Not Secure
Security Of Railway Communication Protocols

36 min
Apple's iPhone 15: Under the C
Hardware hacking tooling for the new iPhone generation
36 min
Unlocking the Road Ahead: Automotive Digital Forensics
A deep dive into an underrepresented research area
39 min
Fuzzing the TCP/IP stack
beyond the trivial
40 min
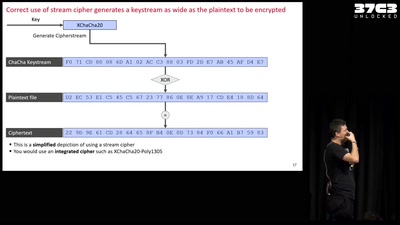
Unlocked! Recovering files taken hostage by ransomware
Decrypting files hijacked by the "second most used…
62 min
Einführung in Smartphone Malware Forensik
Wie man Stalkerware und Staatstrojaner auf Smartphones…
54 min
Oh no: KUNO - Gesperrte Girocards entsperren
Über „Girodays“ & anderen Kuriositäten

40 min
Fuzz Everything, Everywhere, All at Once
Advanced QEMU-based fuzzing
47 min
Finding Vulnerabilities in Internet-Connected Devices
A Beginner’s Guide

42 min
NEW IMPORTANT INSTRUCTIONS
Real-world exploits and mitigations in Large Language Model…

38 min
What your phone won’t tell you
Uncovering fake base stations on iOS devices

42 min
Nintendo hacking 2023: 2008
Finishing off the Nintendo DSi
39 min
Decentralized energy production: green future or cybersecurity nightmare?
The cybersecurity dark side of solar energy when clouds are…
59 min
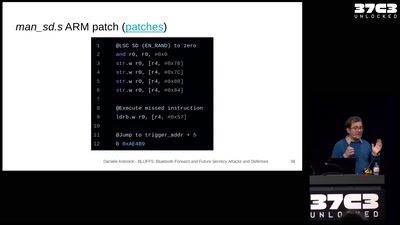
BLUFFS: Bluetooth Forward and Future Secrecy Attacks and Defenses
Breaking and fixing the Bluetooth standard. One More Time.
38 min