15.-19.08.2023, Ziegeleipark Mildenberg, Zehdenick, Germany, Earth, Milky Way
The Chaos Communication Camp is an international, five-day open-air event for hackers and associated life-forms. It provides a relaxed atmosphere for free exchange of technical, social, and political ideas. The camp has everything you need: power, internet, food and fun. Bring your tent and participate!

61 min
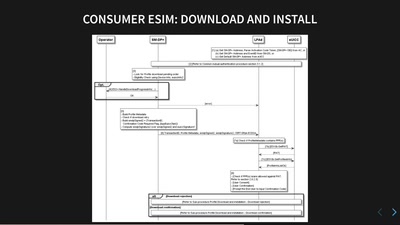
Vacuum robot security and privacy
prevent your robot from sucking your data
47 min
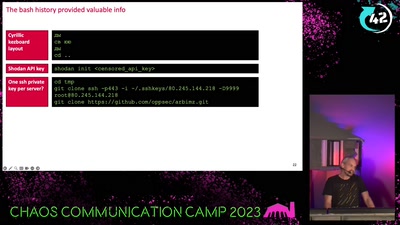
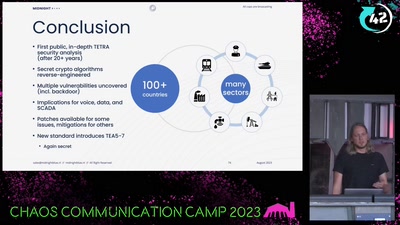
All cops are broadcasting
Obtaining the secret TETRA primitives after decades in the…
43 min
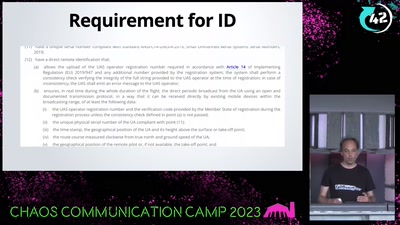
WTF DJI, UAV CTF?!
A hacker's view at commercial drone security
21 min
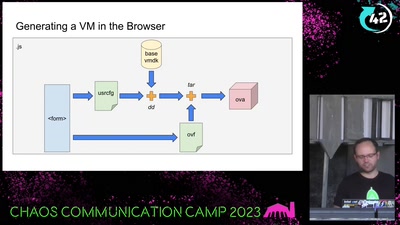
Bootloader Crimes
Building disposable Windows VMs
44 min
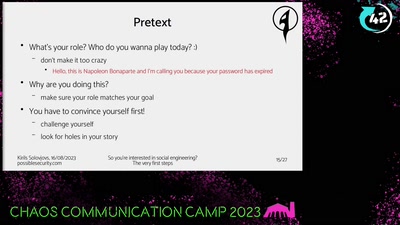
So you're interested in social engineering?
The very first steps

29 min
What de.fac2?
Attacking an opensource U2F device in 30 minutes or less
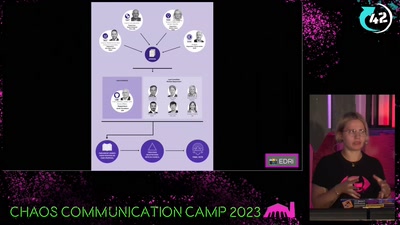
43 min
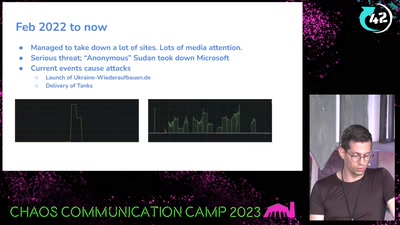
Chat-Control
now is the time to take action!
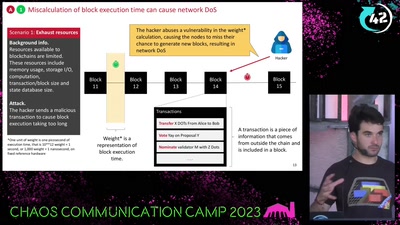
37 min
DON’T PANIC
bytes, blocks, bugs
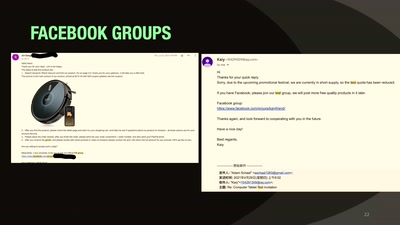
41 min
Our Time in a Product Review Cabal
And the malware and backdoors that came with it.

16 min
For Fox’s Sake
Bypassing Enterprise Policy in Firefox

39 min
Bits and Bytes in Microgravity
Insights into the hardware and software of sounding rockets
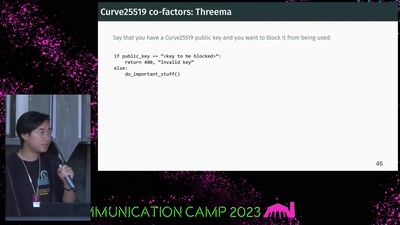
43 min
If It Ain't Broken, Do Fix It
Building Modern Cryptography

20 min