Search for "JO" returned 9867 results
61 min
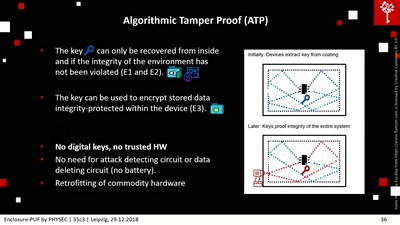
Enclosure-PUF
Tamper Proofing Commodity Hardware and other Applications
51 min
SCADA and PLC Vulnerabilities in Correctional Facilities
Tiffany Rad, Teague Newman, John Strauchs

65 min
Practical RFID Attacks
writing, sniffing & emulating 13.56MHz RFID tags with…
33 min
The Transhumanist Paradox
Deciding between technological utopias in a liberal state

40 min
Settling the IM war
Creating an open and federated protocol for instant…

42 min
Just in Time compilers - breaking a VM
Practical VM exploiting based on CACAO

61 min