Chaos Communication Camp 2007
Full playlist: Video
53 min
A Case Against C++
Why C++ is bad for the environment, causes global warming…

53 min
Know your compiler
...and what the optimizer does so you don't have to

60 min
B.A.T.M.A.N. - Better Approach to Mobile Ad-Hoc Networking
New routing algorithm and daemon for wireless community…

32 min
UAVs, Drohnen, Quadrocopter
md4-200, md4-1000 (hoffentlich), Opensource-Quadrocopter…

65 min
Practical RFID Attacks
writing, sniffing & emulating 13.56MHz RFID tags with…
Security.jpg)
62 min
Antivirus (In)Security
Bugs in Antivirus Software

48 min
Breaking WEP in less than 60 Seconds
the next level

54 min
Swedish analysis of Nazi crypto TTYs
How Beurling et al. broke the Siemens & Halske T52 crypto…
_gegen_die_Stasi_2.0_tun_kannst.jpg)
69 min
Was Du heute (legal) gegen die Stasi 2.0 tun kannst
Widerstand ist nicht zwecklos, wenn er schlau und…

61 min
The A5 Cracking Project
Practical attacks on GSM using GNU Radio and FPGAs
48 min
GPS-Trackers
How they track you when your mobile is switched off
46 min
Tits & Bits
pr0n 2.0
53 min
21st Century digital Bikes
No Gas, No Fee or Tax, No Driver License, what's possible…

47 min
Fun with NFC Mobile Phones
Near Field Communication

64 min
Arguments Against Surveillance
'Cos "I Don't Like It" Is Not Enough!

44 min
GNU Radio & the Universal Software Radio Peripheral
Current Capabilities and Future Directions

43 min
Twisting timing in your favour
Finding and exploiting concurrency issues in software
_forget_your_secret_crypto_key.jpg)
34 min
How to (really) forget your secret crypto key
What you always wanted to know about Flash memory - but…

36 min
Drohnen züchten
UAVs und andere spannende Dinge

55 min
Hack Your Brain
Using Sound & Light Machines to achieve desired states of…
119 min
monochrom's Taugshow #12
A joyful bucket full of good clean fanaticism, crisis,…
98 min
Hardware Hacking for Software Geeks
Essential Tips and Tricks

18 min
Camp Opening Event
Welcome!
65 min
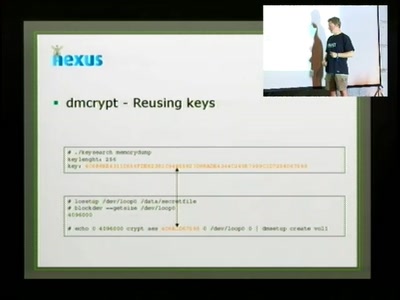
Cryptographic key recovery from Linux memory dumps
Does dm-crypt and cryptoloop provide expected security when…

71 min
Estonia and information warfare
What really happened in Estonia, and what does it mean to…
46 min
Inside Sputnik & OpenBeacon - Smart Dust for the Masses
a hackers guide into homebrewn 2.4GHz hardware & peripherals
41 min
Hacking on the Nanoscale
Dual Beam Devices for Rapid Prototyping and Reverse…
46 min
Proof by Erasure
The Life of John von Neumann

51 min
The School of Hacking Art
Is it possible? 10 years experience from the first man who…

37 min
Hacking Space
Cheap access to Space using lighter then air methods

59 min
Dungeons and Hyperlinks
Electronic Literature and Digital Narratives from Text…

58 min
Geocaching and Alternate Reality Games
Play Simulations of Future Problems

38 min
People, Profiles and Trust
On interpersonal trust in web-mediated social spaces

33 min
Enabling Innovation in Europe
Hacker Spaces, Startups, and a new approach to social…

47 min
WIPO Broadcasting Treaty
Lobbying on an International Scale

47 min
Hacking the Bionic Man
Science fiction or security in 2040?
41 min
Terrorists and the Internet
A Justification for Stricter Laws?
31 min
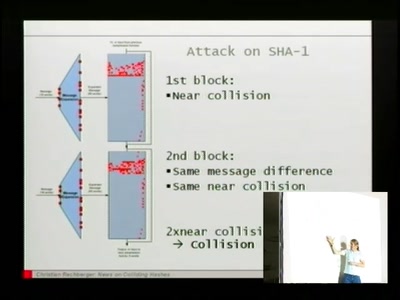
News on Colliding Hashes
The ball is rolling: One of the biggest challenges in…

65 min
ZERT: VML, ANI and Third-party Patches
Assembly - lots of it.

47 min
Rebellious Communication and the Federal Flood
My experience and the role of bloggers, podcasters, and…
56 min
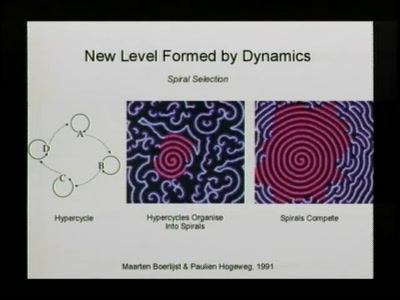
Life & Complexity
Organisation, information and optimisation in real and…
79 min