Search for "floX"
prev
next

61 min
Cybernetics, Anti-Terrorism, and the ongoing case against…

64 min
Dissecting a Modern Wireless Network for the Internet of…

58 min
Possible paths from today's ghastly hackery to what…

58 min
Export controls and exploit regulations: braindead and…
58 min
A survey of BSD kernel vulnerabilities.

54 min
An introduction to reverse engineering network protocols

32 min
Math, Functional Programming, Theorem Proving, and an…
53 min
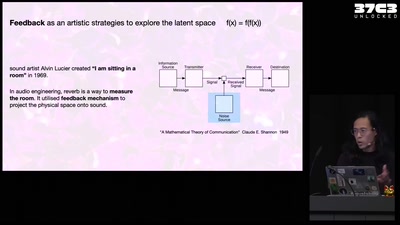
Artistic Strategies to expose generative text-to-image…
38 min
Mit Tools & Methoden dem Vertrag auf den Zahn fühlen

45 min
Digital Identity Systems in the EU & around the world
prev
next






