Search for "Andi" returned 7269 results
28 min
Solar-powering your Geek Gear
Alternative and mobile power for all your little toys
41 min
Hacking on the Nanoscale
Dual Beam Devices for Rapid Prototyping and Reverse…

63 min
What's the catch?
Funding open source with money from corporations and…

40 min
Crypto Dawn
A To Do list for Cyptographic Research and Implementations

60 min
Internet Cube
Let's Build together a Free, Neutral and Decentralized…

61 min
The A5 Cracking Project
Practical attacks on GSM using GNU Radio and FPGAs
32 min
Cryptokids
empower kids and provide tools for them to be more secure…

26 min
Data Mining for Good
Using random sampling, entity resolution, communications…
58 min
Confessions of a future terrorist
A rough guide to over-regulating free speech with…

38 min
Honey, let's hack the kitchen:
Attacks on critical and not-so-critical cyber physical…
35 min
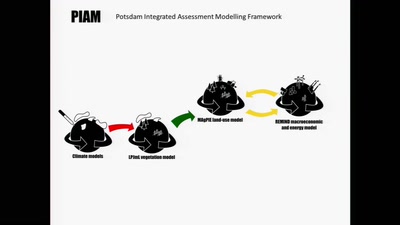
Simulating the future of the global agro-food system
Cybernetic models analyze scenarios of interactions between…
49 min
SD-WAN a New Hop
How to hack software defined network and keep your sanity?

52 min
SiliVaccine: North Korea's Weapon of Mass Detection
How I Learned to Stop Worrying and Love the Backdoor

60 min
A brain is not a computer
Insights into neurology and psychological behaviours…

60 min
The Hash Disaster
Recent Results on Cryptanalysis and their Implications on…

62 min
GUERRILLA.COM
How to mess with media, the market and life itself

60 min
Profiling (In)justice
Disaggregating Data by Race and Ethnicity to Curb…

49 min
Access to Knowledge
Copyright, Patents and Politics at the World Intellectual…

31 min
openSUSE ALP prototype on AWS, experimental, but fun!
Experiences, challenges and how SUSE NeuVector came into…

37 min
Eliminating the database bottleneck for proper horizontal scalability
Using embeddable databases to allow true and simple…
38 min
The importance of performance testing in the NFV world
Challenges and state-of-the-art in the OPNFV community
35 min
Ethics in the data society
Power and politics in the development of the driverless car

49 min
BREACH in Agda
Security notions, proofs and attacks using dependently…

76 min
Information Operations
Sector-Oriented Analysis of the Potential Impact and…

100 min