59 min
How the NSA tracks you
Perspective from the inside
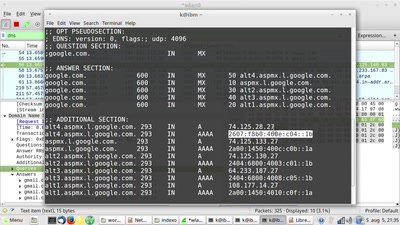
156 min
Network concepts introduction & wireshark workshop
The legendary workshop that teaches you how network really…

33 min
Social cooling
How the reputation economy is turning us into conformists
62 min
A trip to India
Hunting down a criminal call center
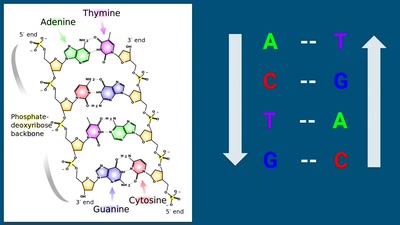
61 min
DNA: The Code of Life
Surprise: it is fully digital!
30 min
Best of IoT Fails
When reality beats science fiction
54 min
DDoS attack and defense
for the lulz

57 min
Black Hat Locksmithing
When Locksmiths Go Bad
54 min
Infrastructure review
How all the infra teams made SHA2017 possible
61 min
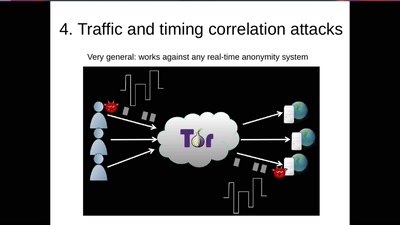
Tor de-anonymization techniques
How people have lost their anonymity? Let's study…
56 min
Hack-a-ble
Hacking BLE Smart Devices
![NSFW: Di[CENSORED]s for privacy](https://static.media.ccc.de/media/events/SHA2017/49-hd.jpg)
28 min
NSFW: Di[CENSORED]s for privacy
Why not give hackers and agencies something to look at . .
53 min
How an intern hacked the powergrid
The Horus Scenario

56 min
Blockchains for a Better World
From Napster to Bitcoin to Ethereum to Statebox: saving the…

49 min
MISP threat sharing platform
The MISP threat sharing platform is a free and open source…

61 min
FaceDancer 2.0
easy USB hacking, sniffing, and spoofing

25 min
Network Traffic Analysis using Deep Packet Inspection and Data Visualization
Eventpad: the Sublime editor for network traffic
60 min
Nerd-Wrangling 101
Managing Neurodiversity with Cognitive Empathy
44 min
Legacy Crypto Never Dies
Cracking DES nearly 20 years after the EFF DES Cracker

43 min
Hack North Korea
Flash Drives for Freedom

47 min
Decentralize! Self-hosting in your own home using Sovereign
act up on decentralization
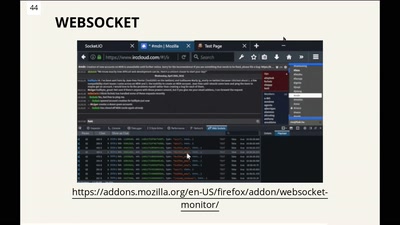
48 min
Demolish the web with the Firefox Dev Tools!
Do you know what you can do with Firefox for frontend…

57 min
Biometric ID cards by the billion
Experiences with Aadhaar in India, or what possibly could…
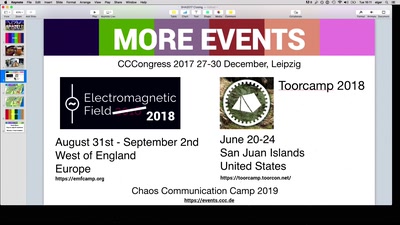
29 min
SHA2017 Closing
Five days of hacking, this is what happened. You wouldn't…

28 min
Exploiting The North American Railways
Modern Day American Hobo-ism

50 min
Bypassing Secure Boot using Fault Injection
Bypassing Secure Boot using Fault Injection
38 min
Hacking on a boat
Fun with onboard maritime systems

39 min
My Safe In Your House
Keeping Secrets On Remote Machines
62 min
Let There be Light
Adventures in LED Lighting
49 min
Attacking OpenSSL using Side-channel Attacks
The RSA case study

27 min
Detecting a breach from an attackers perspective.
We're gonna regret this
58 min
OpenINTEL: digging in the DNS with an industrial size digger
I measured 60% of the DNS, and I found this
40 min
Improving security with Fuzzing and Sanitizers
Free and open source software has far too many security…

36 min
Parkour communications
How you can communicate, free running style, using nothing…
29 min
Hormones and Hysteria - what every person should know
are you not curious now? ;)

55 min
Because "use urandom" isn't everything: a deep dive into CSPRNGs in Operating Systems &…
Implementation, hazards and updates on use of RNGs in…

57 min
Cryptowars 2.0: Lessons from the past, for the present
It's not only Hollywood who is out of ideas
48 min
The Hackeboy handheld game console
Retro-gaming on open hardware

61 min
Resisting Algorithms of Mass Destruction
#NotMyDebt Australia
17 min
"Information. What are they looking at?"
A documentary on privacy for the broad audience.

56 min
Let's hack words
Creative Writing

51 min
Anonymous, secure and easy. You can have them all.
An authentication protocol that offers security, privacy…
43 min
Get your ass (HTTP infrastructure) on TLS
It's about the time.
23 min
SHA2017 Opening
Heaven is imperfect by design
36 min
Smart Home Security with Tor
Using TOR for securing Smart Homes from prying eyes

26 min
Silent Protest
DIY wearable protest network

61 min
The state of the pretty Easy privacy (p≡p) project and what to expect next
Easy to use automatic encryption for the masses

25 min
Hackerspaces Jedi
Everything is interconnected - but how?
24 min
Responsible Disclosure; How to make your school a safer place.
Story of a 15 year old hacker in collaboration with his…

46 min
SHOULD I STAY OR SHOULD I GO?
THE ALGORITHMIC PUBLIC SPHERE AND YOU

53 min
TBM: Trusted boot module
NLNet sponsored (open hardware) trusted boot module

52 min
Privacy Design Strategies
Doing well is good enough

63 min
Data Exploitation
how your digital doppelganger has been exploiting you all…
58 min
(In)discrete Music
(mis)adventures in generative art
18 min
Malware: From your text editor, to the United States Government's Lab
How Universities in the US collaborate with the United…
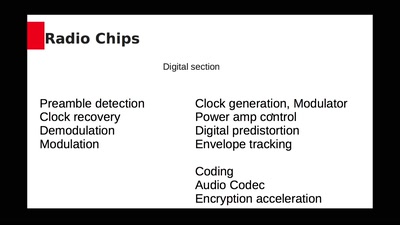
23 min
Failure modes of digital radios
World radio spectrum domination through silicon control
43 min
The quest for algorithm diversity
facebook.tracking.exposed

48 min
Computational Thinking
How your can teach it.

40 min
I have a dream
The ultimate Hackerspace; From Panopticon-prison to…

60 min
When Tech MIMICS Reality
Identity and Agency In the Age of Algorithms

81 min
Energy Harvesting for Smart Autonomous Electronics 2
Towards a future of autonomous wireless electronics without…

34 min
The Fenrir Project
Fixing Authentication and Transport protocols

40 min
The World in 24 Hours Revisited
How to re-enact a 1982 network art performance

36 min
From Project To Kit
Bringing an electronic project to market in kit form

61 min
Human body as an electric IO system
Hacking your brain, and other body parts. Debunking myths…

52 min
An academic's view to incident response
It's all fun and games until reality starts kicking you in…

60 min
Flip Feng Shui
Advanced Rowhammer exploitation on cloud, desktop, and…

50 min
from glass fiber to fiber glass noodles
towards edible network infrastructures
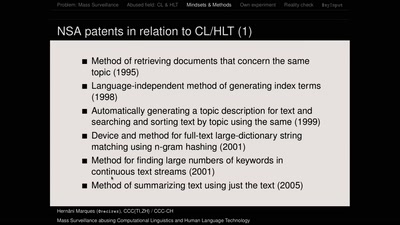
59 min
Mass Surveillance abusing Computational Linguistics and Human Language Technology
Mind-sets, state-of-the-art methods and practices according…

53 min
Moving towards fully encrypted web
Checkpoint on the road towards inevitable

37 min
One map to map them all
Why MissingMaps saves lives, and how to help
42 min
Beyond the Titanic
Learning from dataleaks
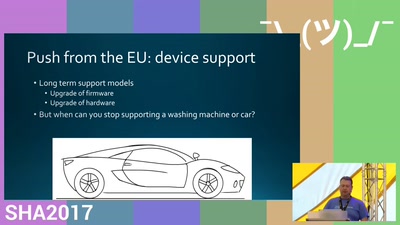
51 min
Playing defence is complicated
What goes into playing defence and what can be holding you…
45 min
Off<>zz Code and Piano Concert
“Code Our Glance” and beta “CodeKlavier”

39 min
Digital dissent in Latin America
How the Internet is impacting organizing and dissent in…

30 min
Gems are truly outrageous
Combining 3D printing and crystallisation techniques
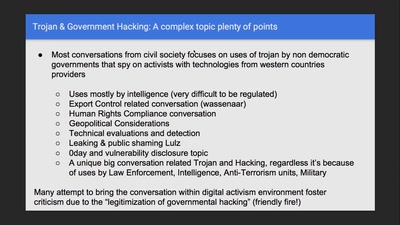
49 min
Regulating Law Enforcement use of Trojans
Implementing a Law to juridically, operationally and…
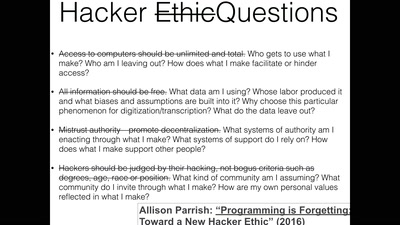
60 min
Ethics in Technology
Internet Measurements' Ethical Dilemmas and RIPE Atlas
32 min
Cryptokids
empower kids and provide tools for them to be more secure…

35 min
Weaponized Social
Understanding and tools to mitigate network-scale violences

50 min
Art Tech Activism Privacy and Cool Robots
Not only hackers do Security, Privacy and Hacking. Want to…

34 min
Digital personal locker
New paradigm in handling personal (health) data

47 min
Olmogo - because it's your data!
A cryptographically secure social network platform
68 min
Neuralscape Bowels
How to read brainwaves using cheap toys

64 min
Fermentation Mobile
experimental, educational and commercial fermentation…

53 min
Smart, safe & happy
ensuring civil rights in the digital era

52 min
Human Rights and Internet Infrastructure
standard or substandard?
64 min
Are Whistleblowers safer today than they were at OHM2013?
Current case studies of whistleblowing in Europe, and how…
48 min
Cut by the free and open edge
FLOSS, NGOs, Activists, Journalists, and the Pareto…

41 min
Software Patents v3.0: the Unitary Patent Court
Have we silently lost the battle against software patents…

21 min
Good is hard, but try anyway.
Ethics, colonialism, technological optimism and the reality…

57 min
Building Businesses that we can Buy Into and Believe In
What it means to profit from privacy-friendly, open-source…

38 min
Hardware games
How to build alternative controllers

33 min
Copyfighters
How can we make sure that young people's voices are heard…
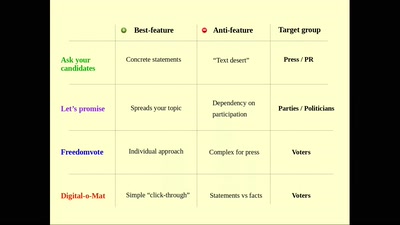
41 min
Ask your candidates and let everyone know about it
How to make use of democratic elections for your own purpose

59 min
Developments in Coordinated Vulnerability Disclosure
The government is here to help

27 min
The law and leaky abstractions
In what ways can laws influence the security of society.

44 min
Life Needs Internet
Documenting digital culture through handwritten letters

74 min
Let's stop EU copyright expansion
If you like untaxed links and unsurveilled uploads, you…
58 min