58 min
How to Destroy a Laptop with Top Secrets
How did GCHQ do it to the Guardian's copy of Snowden's…

58 min
Kissing – Heiße Tipps und Techniken
Keeping it short & simple. Oder: Wozu man Hunde mit…
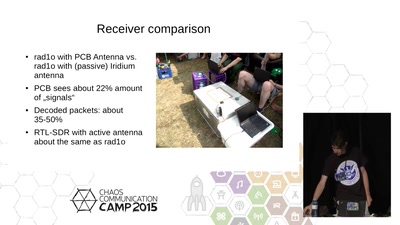
46 min
Iridium Hacking
please don't sue us

28 min
Mexican Botnet Dirty Wars
Bots are waging a dirty war in Mexican social media.

31 min
Update: Vor Windows10 Update Warnung
Update (Patch) Debakel

56 min
NSA-Untersuchungsausschuss - Wer kontrolliert wen?
Zwischen den geschwärzten Zeilen lesen

104 min
The Incredible Herrengedeck
Chanson-Punk aus Berlin

109 min
Freak Show
Live-Podcast on Stage
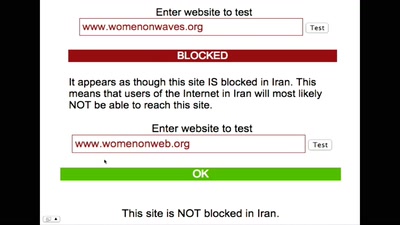
54 min
Drones, ships, pills and the Internet
Women on waves

30 min
Chaos Communication Camp Opening
Welcome!

40 min
Crypto Dawn
A To Do list for Cyptographic Research and Implementations

31 min
Freifunk in TV-Whitespace
More frequency spectrum with better propagation properties…

32 min
Kontrolle ist gut. #Landesverrat ist besser.
Wie eine investigative Recherche zum geheimen Ausbau der…
55 min
How to make your software build reproducibly
Get a verifiable path from source to binary

48 min
3D Printing High-Quality Low-Cost Free Medical Hardware
Making medical devices accessible and hackable for all
46 min
Bugged Files
Is Your Document Telling on You?

60 min
Mythen der Elektronikentwicklung
„Der Profi macht nur neue Fehler. Der Dummkopf wiederholt…

51 min
Die Reichstagswiese umgraben und Drecksfirmen hacken
Neue Perspektiven und Ideen für zivilen Ungehorsam

54 min
20 Jahre c-base
Die Wahrheit™ über den Absturz - eine Transparenzoffensive

55 min
Encrypted Email for Planet Earth
Failures, Challenges, and the Future
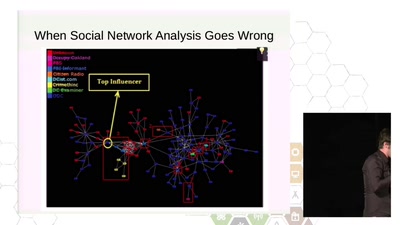
60 min
Resisting Surveillance: it's is not just about the metadata
The infiltration and physical surveillance of social…
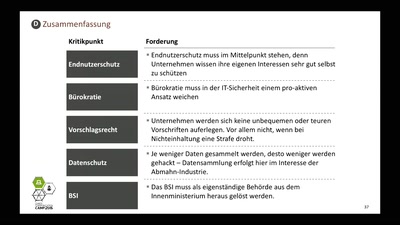
36 min
Politische Lösungen für technische Probleme?
IT-Sicherheit per Gesetz

54 min
Staatstrojaner in Karlsruhe
Anhörung zur verdeckten Infiltration von IT-Systemen
48 min
Advanced interconnect attacks
Chasing GRX and SS7 vulns

29 min
Basics of hydroponics
A need to know on soilless growing before building,…
28 min
Hardware attacks: hacking chips on the (very) cheap
How to retrieve secret keys without going bankrupt

30 min
Privacy Badger
Stop being tracked online

22 min
Chaos Communication Camp Closing
Goodbye!

30 min
A Torifying Tale
Our experiences of building and running Tor servers

31 min
Wo das Internet lebt
Eine Such-Reportage nach der physischen Seite des Netz
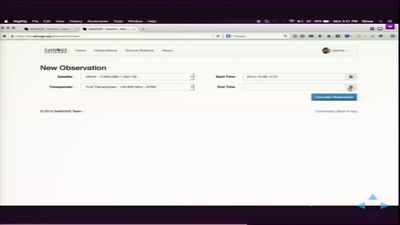
25 min
Satellite Open Ground Station Network
open source ground station, optimized for modularity, built…
![for women in "${tech[@]}"; do](https://static.media.ccc.de/media/conferences/camp2015/6774-hd.jpg)
26 min
for women in "${tech[@]}"; do
Let's talk, share and learn from each other.
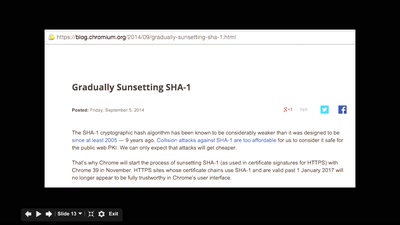
42 min
Let's Encrypt
A Certificate Authority To Encrypt the Entire Web
20 min
How To Become A Space Hacker
(let's hack OUTER space, the final frontier)

30 min
D-Offline? Das drohende WLAN-Sterben & was wir dagegen tun können
Die Bundesregierung will offene WLANs verhindern, aber das…
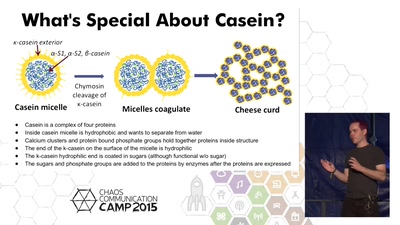
30 min
Real Vegan Cheese
Engineering yeast to produce casein
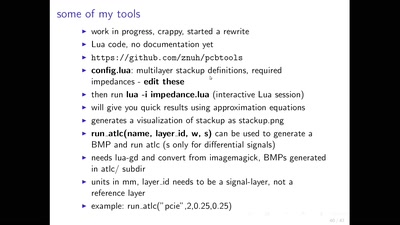
59 min
Pushing the limits of DIY electronics
Bridging the gap between DIY and professional electronics

29 min
Jumping the Paywall
How to freely share research without being arrested

16 min
o͈̮p̢ęr̕a͠t̶̨i͟oǹ͓̜a̵l̷ glit̶̨ć̶̛he͝s
How To Make Human Machine Readable
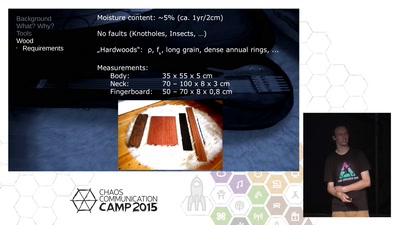
60 min
A Hackers Approach To Building Electric Guitars
Let's do everything except the pots by ourselves
47 min
FPGAs for everyone
Integrating FPGAs with standard personal computers

22 min
Freie Software gegen unsere Freiheit?
Fighting code-abuse by military and intelligence

63 min
Refugees Emancipation
Bringing Internet access to those who need it most.

34 min
Digital Musical Instruments
Evolution and design of new interfaces for musical…

28 min
Gotta Block’em all
Creating a usable tool against online trackers
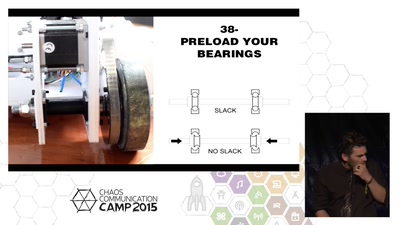
30 min
A practical prototyping primer
A rather unstructured selection of things I wished I knew…

54 min
Singing Capacitors and Whining Inductors
A Practical Introduction to Acoustic Cryptanalysis
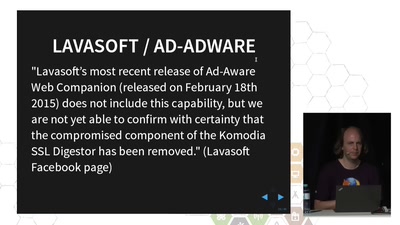
52 min
TLS interception considered harmful
How Man-in-the-Middle filtering solutions harm the security…

21 min
Goethe in my Mind
Computer haben Gefühle, wir helfen ihnen, sie auszudrücken

63 min
What's the catch?
Funding open source with money from corporations and…

58 min
Terraforming Planet Earth
Practical terraforming technologies for regenerating soils…

27 min
Analogue Mission Simulations
Wait what? Why not digital?

30 min
The quest for artificial general intelligence
beyond the Turing test

24 min
Building your First Combat Robot
Nothing shows pride like letting others destroy what you’ve…

60 min
Living with the lasersaur
Experiences with the open source laser cutter

59 min
Detecting echoes from the dawn of time
Nifty technologies behind the world's most sensitive…

26 min
Data and discrimination: representing marginalised communities in data
The right to be counted, or the right to be left alone?
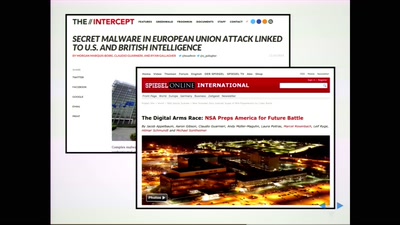
56 min
Helping the Helpless
Targeted threats to civil society

122 min
c-base birthday event
20 years of c-base

30 min
Satellite Imagery in Agriculture
Questioning privacy, data protection, and autonomy in the…

275 min
c-base birthday party
20 years of c-base party
69 min
The hills are alive with the sound of hacking ... don't wake the monkeys!
The State of the Hack in India. A place to be^W hack in the…

36 min
Mier – failure attempt to CC license as mass market consume good
A creative drink for the commons
31 min
Hackerfleet - what happend?
Opensource and Venture Capital, Softwaredevelopment and…

45 min
Fueling the Revolution
Personal production of bio-fuels

44 min
Hackerfleet - what happend?
Discussion round

27 min