Guillaume Dupont and Alexios Lekidis
For a long time automobile manufacturers designed their cars as closed systems with no security in mind. Recently security researchers have demonstrated how vulnerable vehicles are to cyber-attacks. Once compromised the vehicle is at the mercy of the hackers: by remotely taking over control of the car, they can perform dramatic actions with severe safety-related consequences for the passengers.
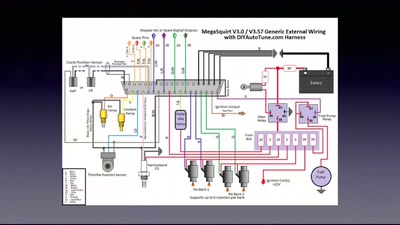
This issue comes from the design of automobiles and the communication protocols they use. To function properly a vehicle makes use of different computers called “Electronic Control Units” (ECU) to perform various operations such as breaking or steering. Connected all together on the in-vehicle networks, the ECUs communicate with each other using simple protocols involving no security features, assuming the legitimacy and the trustworthiness of their peers. The lack of security mechanisms makes it difficult to guarantee the confidentiality, integrity and availability of automotive systems. Moreover the complexity of the situation increases with the rise of connected vehicles, communicating with each other (Vehicle-2-Vehicle communications, V2V) and with the infrastructure (Vehicle-2-Infrastructure communications, V2I).
#PhysicalSecurity #DeviceSecurity #NetworkSecurity #IoT