Events for tag "25c3"

103 min
Hacker Jeopardy
Die ultimative Hacker-Quizshow

57 min
Rapid Prototype Your Life
The time is now to make anything you can imagine

62 min
Security and anonymity vulnerabilities in Tor
Past, present, and future

65 min
Terrorist All-Stars
Some cases of terrorism around the world that are not…
33 min
Repurposing the TI EZ430U
with msp430static, solder, and syringe

61 min
Der Hackerparagraph 202c StGB
Bestandsaufnahme und Auswirkungen

50 min
Fnord News Show
Wir helfen Euch, die Fnords zu sehen

125 min
Jahresrückblick
Die Themen des CCC im Jahr 2008

61 min
MD5 considered harmful today
Creating a rogue CA Certificate

58 min
Collapsing the European security architecture
More security-critical behaviour in Europe!

58 min
The Infinite Library
Storage and Access of Pornographic Information
55 min
All your base(s) are belong to us
Dawn of the high-throughput DNA sequencing era
58 min
Advanced memory forensics: The Cold Boot Attacks
Recovering keys and other secrets after power off

82 min
Attacking NFC mobile phones
First look at the security of NFC mobile phones

51 min
Algorithmic Music in a Box
Doing music with microcontrollers
63 min
Exploiting Symbian
Symbian Exploit and Shellcode Development
65 min
eVoting after Nedap and Digital Pen
Why cryptography might not fix the issue of transparent…

45 min
Privacy in the social semantic web
Social networks based on XMPP
58 min
Hacking the iPhone
Pwning Apple's Mobile Internet Device
60 min
Flying for free
Exploiting the weather with unpowered aircraft
57 min
Zehn Big Brother Awards in .at
Rückblick über eine bewegte Zeit

50 min
Predictable RNG in the vulnerable Debian OpenSSL package
the What and the How

76 min
Messing Around with Garage Doors
Breaking Remote Keyless Entry Systems with Power Analysis
67 min
Life is a Holodeck!
An overview of holographic techniques
50 min
FAIFA: A first open source PLC tool
PowerLineCommunications has now their open source tool

65 min
Blinkenlights Stereoscope
Behind the scenes of the new light installation

53 min
Short Attention Span Security
A little of everything

65 min
Building an international movement: hackerspaces.org
What we did so far. What will happen in the future.

59 min
Embracing Post-Privacy
Optimism towards a future where there is "Nothing to hide"

49 min
Beyond Asimov - Laws for Robots
Developing rules for autonomous systems

44 min
Why technology sucks
If technology is the solution, politicians are the problem

50 min
Fnord News Show (English interpretation)
We help in seeing teh Fnords

48 min
SWF and the Malware Tragedy
Hide and Seek in A. Flash

55 min
Das Grundrecht auf digitale Intimsphäre
Festplattenbeschlagnahme in neuem Licht

58 min
Security Failures in Smart Card Payment Systems
Tampering the Tamper-Proof

102 min
Hacker Jeopardy (English interpretation)
The ultimative Hacker-Quizshow

37 min
Cracking the MSP430 BSL
Part Two

61 min
Lightning Talks Day4
4 minutes of fame

48 min
The Privacy Workshop Project
Enhancing the value of privacy in todays students view
66 min
Cisco IOS attack and defense
The State of the Art
30 min
TCP Denial of Service Vulnerabilities
Accepting the Partial Disclosure Challenge

52 min
Objects as Software: The Coming Revolution
How RepRap and physical compilers will change the world as…

48 min
Not Soy Fast: Genetically Modified, Resource Greedy, and coming to a Supermarket Near You
The silent march of the multinational GMO soy industry and…
55 min
Lightning Talks Day3 - Evening
4 minutes of fame
94 min
Security Nightmares 2009
Oder: worüber wir nächstes Jahr lachen werden
28 min
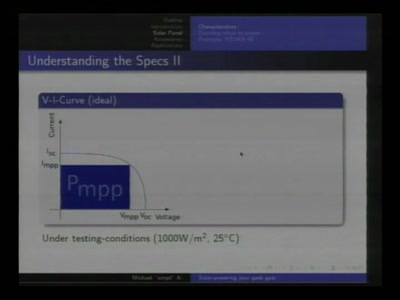
Solar-powering your Geek Gear
Alternative and mobile power for all your little toys

48 min
Vertex Hacking
Reverse Engineering von 3D-Dateiformaten

70 min
Neusprech im Überwachungsstaat
Politikersprache zwischen Orwell und Online
63 min
Banking Malware 101
Overview of Current Keylogger Threats

47 min
Kurt Gödel – I do not fit into this century
Ein audiovisuelles Live-Feature

44 min
About Cyborgs and Gargoyles
State of the Art in Wearable Computing

71 min
Soviet Unterzoegersdorf
A Nation In Transit

56 min
Console Hacking 2008: Wii Fail
Is implementation the enemy of design?

50 min
coreboot: Beyond The Final Frontier
Open source BIOS replacement with a radical approach to…

61 min
Attacking Rich Internet Applications
Not your mother's XSS bugs

66 min
La Quadrature du Net - Campaigning on Telecoms Package
Pan-european activism for patching a "pirated" law

39 min
Scalable Swarm Robotics
Formica: a cheap, open research platform
35 min
Tricks: makes you smile
A clever or ingenious device or expedient; adroit…

52 min
Datenpannen
Forderungen nach dem Jahr der Datenverbrechen

38 min
Squeezing Attack Traces
How to get useable information out of your honeypot
56 min
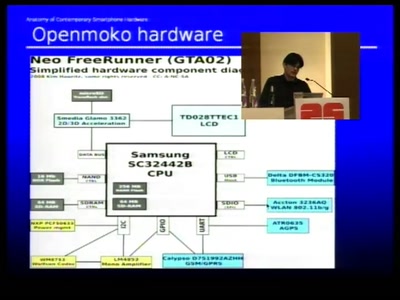
Anatomy of smartphone hardware
Dissecting contemporary cellphone hardware

54 min
Pflanzenhacken
Züchten 2.0

44 min
Just Estonia and Georgia?
Global-scale Incident Response and Responders

44 min
OnionCat – A Tor-based Anonymous VPN
Building an anonymous Internet within the Internet

92 min
Security Nightmares 2009 (English interpretation)
Or: about what we will laugh next year
59 min
Lightning Talks Day3 - Morning
4 minutes of fame
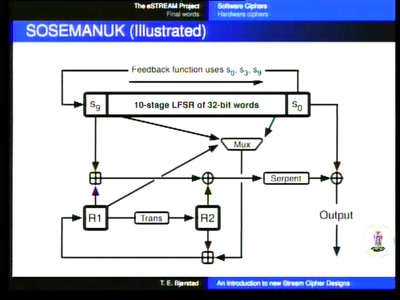
46 min
An introduction to new stream cipher designs
Turning data into line noise and back
48 min
Full-Disk-Encryption Crash-Course
Everything to hide
51 min
Lightning Talks Day2
4 minutes of fame

60 min
Der elektronische Personalausweis
Endlich wird jeder zum "Trusted Citizen"

51 min
Erich Mühsams Tagebücher in der Festungshaft
Ein Idylle aus der Analogsteinzeit der Überwachung

61 min
Handschellen hacken
Essentielles Grundwissen für alle, die nichts zu verbergen…

60 min
The Trust Situation
Why the idea of data protection slowly turns out to be…
61 min