Search for "Lee" returned 2381 results

51 min
Uncovering vulnerabilities in Hoermann BiSecur
An AES encrypted radio system

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

47 min
Hardening hardware and choosing a #goodBIOS
Clean boot every boot - rejecting persistence of malicious…

59 min
TamaGo - bare metal Go framework for ARM SoCs.
Reducing the attack surface with pure embedded Go.

60 min
net neutrality: days of future past?
Taking stock after two years of net neutrality in the…
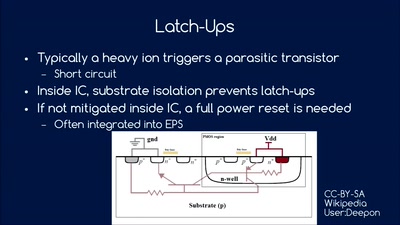
60 min
So you want to build a satellite?
How hard can it be? An introduction into CubeSat development

40 min
Radical Digital Painting
Fantastic Media Manipulation

58 min
Thwarting Evil Maid Attacks
Physically Unclonable Functions for Hardware Tamper…

61 min
Warum die Digitale Revolution des Lernens gescheitert ist.
Fünf Desillusionen
31 min
The Economic Consequences of Internet Censorship
Why Censorship is a Bad Idea for Everyone

59 min
Memory Deduplication: The Curse that Keeps on Giving
A tale of 3 different memory deduplication based…

25 min
Regulating Autonomous Weapons
The time travelling android isn’t even our biggest problem
30 min