Search for "JO" returned 10046 results
55 min
Cat & Mouse: Evading the Censors in 2018
Preserving access to the open Internet with circumvention…
32 min
Mangrove Conservation via Satellite
using the latest technology to map and monitor mangroves

27 min
Heroes, not Superheroes
What the Heroes would prefer not to tell you ;-)

57 min
Cybercrime Convention
Hacking on its way to become a criminal act?
45 min
USB-Stick zähmen leicht gemacht
Verteidigung gegen BadUSB & Co. für 30 Euro oder weniger

30 min
libusb: Maintainer fail
How I failed to run an open source project
59 min
Ich werde jetzt Embedded-Linux-Entwickler!
“Das kann doch nicht so schwer sein - ist doch auch nur…

31 min
Demystifying Network Cards
Things you always wanted to know about NIC drivers

40 min
The World in 24 Hours Revisited
How to re-enact a 1982 network art performance
17 min
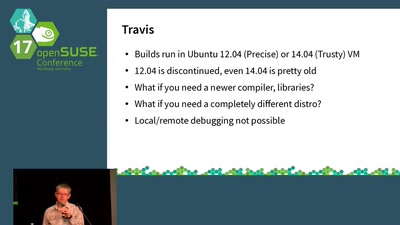
Continuous Integration using Travis and Docker
There is no excuse for NOT using continuous integration

29 min
Open vSwitch and DPDK - Your VMs deserve better
Using OvS + DPDK to boost inter-VM network traffic
37 min
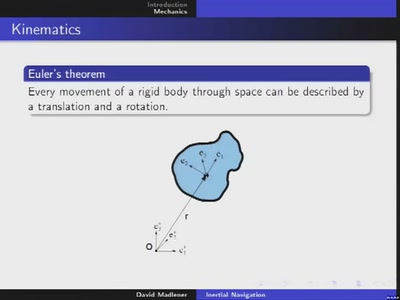
Inertial navigation
Rigid body dynamics and its application to dead reckoning

59 min
10GE monitoring live!
How to find that special one out of millions
53 min
Crouching Powerpoint, Hidden Trojan
An analysis of targeted attacks from 2005 to 2007

59 min
Let Them Fail
An Introduction to Massively Distributed Finance or "Cloud…

45 min
Further hacks on the Calypso platform
or how to turn a phone into a BTS

39 min
DIY Survival
How to survive the apocalypse or a robot uprising

56 min
Smartes Smart Home mit Home Assistant
So geht der Start in das Smart Home auch für dich!

37 min
Eliminating the database bottleneck for proper horizontal scalability
Using embeddable databases to allow true and simple…
36 min
Artistic PCB Design and Fabrication
From doodle to manufacture: how I make mechanically…

49 min
Mining Search Queries
How to discover additional knowledge in the AOL query logs

53 min
Towards a Single Secure European Cyberspace?
What the European Union wants. What the hackerdom can do..

61 min
SMS-o-Death
From analyzing to attacking mobile phones on a large scale.

60 min
the possibility of an army
phone verified accounts bringing the Hessian army back to…

26 min