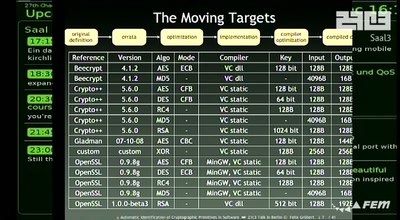
44 min
Console Hacking 2010
PS3 Epic Fail

51 min
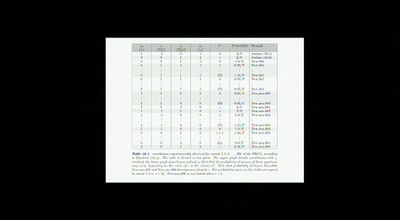
Reverse Engineering the MOS 6502 CPU
3510 transistors in 60 minutes
55 min
Desktop on the Linux... (and BSD, of course)
you're doing it confused? weird? strange? wrong?
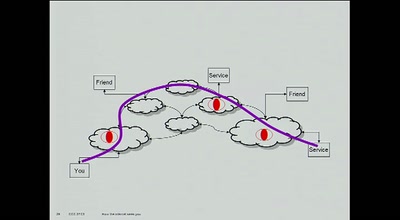
58 min
How the Internet sees you
demonstrating what activities most ISPs see you doing on…
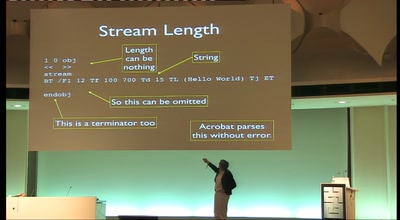
57 min
OMG WTF PDF
What you didn't know about Acrobat

83 min
Fnord-Jahresrückblick 2010
von Atomausstieg bis Zwangsintegration

60 min
"Die gesamte Technik ist sicher"
Besitz und Wissen: Relay-Angriffe auf den neuen…

134 min
Hacker Jeopardy
Number guessing for geeks
35 min
Logikschaltungen ohne Elektronik
logische Schaltungen mit Pneumatik
39 min
Cybernetics for the Masses
implants, sensory extension and silicon - all for you!
56 min
The importance of resisting Excessive Government Surveillance
Join me in exposing and challenging the constant violations…

56 min
JTAG/Serial/FLASH/PCB Embedded Reverse Engineering Tools and Techniques
a dump of simple tools for embedded analysis at many layers

61 min
Running your own GSM stack on a phone
Introducing Project OsmocomBB

63 min
Ich sehe nicht, dass wir nicht zustimmen werden
Die Sprache des politischen Verrats und seiner…

39 min
27C3 Keynote
We come in Peace
58 min
Reverse Engineering a real-world RFID payment system
Corporations enabling citizens to print digital money
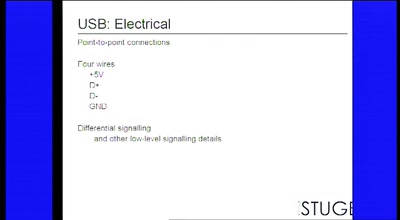
56 min
USB and libusb
So much more than a serial port with power

61 min
SMS-o-Death
From analyzing to attacking mobile phones on a large scale.

65 min
Cognitive Psychology for Hackers
Bugs, exploits, and occasional patches
66 min
The Baseband Apocalypse
all your baseband are belong to us
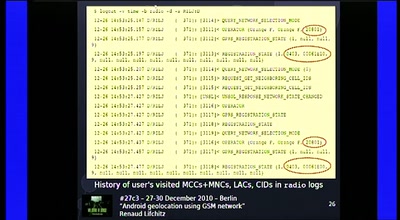
63 min
Android geolocation using GSM network
"Where was Waldroid?"

68 min
"Spoilers, Reverse Green, DECEL!" or "What's it doing now?"
Thoughts on the Automation and its Human interfaces on…
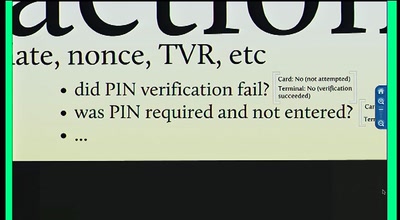
57 min
Chip and PIN is Broken
Vulnerabilities in the EMV Protocol

58 min
Is the SSLiverse a safe place?
An update on EFF's SSL Observatory project

58 min
Analyzing a modern cryptographic RFID system
HID iClass demystified
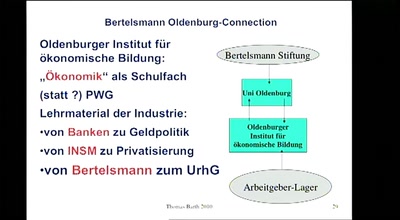
52 min
Netzmedienrecht, Lobbyismus und Korruption
Wie wirkt die Lobby von Medienkonzernen?
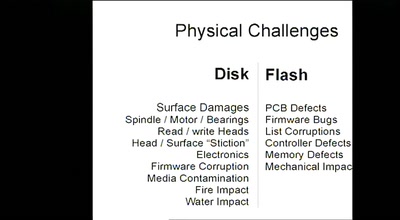
60 min
Data Recovery Techniques
Fun with Hard Drives

64 min
Defense is not dead
Why we will have more secure computers - tomorrow
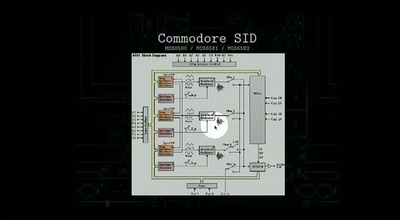
24 min
DIY synthesizers and sound generators
Where does the sound come from?
47 min
The Hidden Nemesis
Backdooring Embedded Controllers

56 min
"The Concert"
a disconcerting moment for free culture
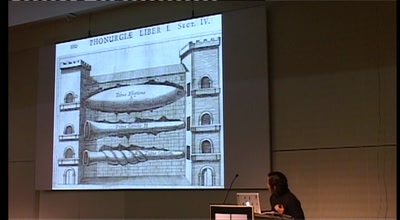
49 min
A short political history of acoustics
For whom, and to do what, the science of sound was…

78 min
Radio der Zukunft
Was kommt nach dem analogen Radio?
35 min
AllColoursAreBeautiful
interactive light installation inspired by blinkenlights
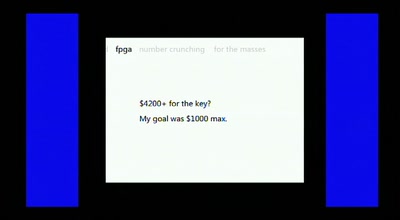
56 min
Distributed FPGA Number Crunching For The Masses
How we obtained the equivalent power of a Deep Crack for a…
73 min
hacking smart phones
expanding the attack surface and then some
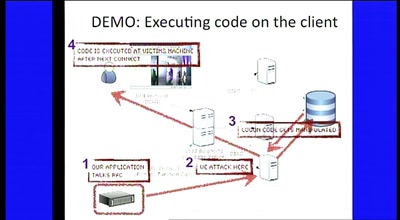
76 min
Rootkits and Trojans on Your SAP Landscape
SAP Security and the Enterprise

64 min
Tor is Peace, Software Freedom is Slavery, Wikipedia is Truth
The political philosophy of the Internet

59 min
Whistleblowing
Licht ins Dunkel!

64 min
Pentanews Game Show
Your opponents will be riddled as well

34 min
Lying To The Neighbours
Nasty effects with tracker-less BitTorrent

59 min
Part-Time Scientists
One year of Rocket Science!
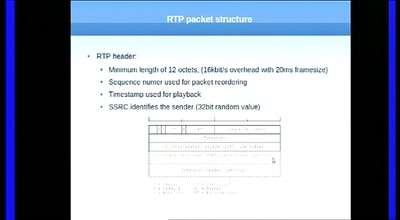
36 min
Having fun with RTP
„Who is speaking???“
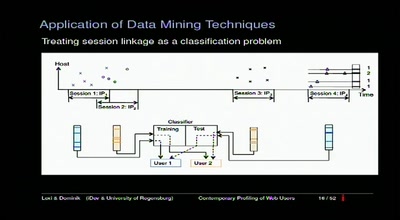
54 min
Contemporary Profiling of Web Users
On Using Anonymizers and Still Get Fucked

54 min
Friede sei mit Euren Daten
Ein datenschutzrechtlicher Ausflug in ein kirchliches…

79 min
Netzneutralität und QoS - ein Widerspruch?
Fakten auf den Tisch
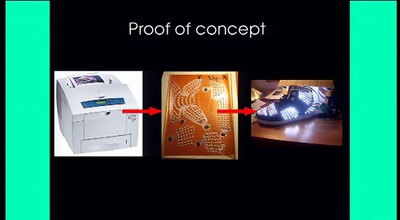
51 min
File -> Print -> Electronics
A new circuit board printer will liberate you from the…
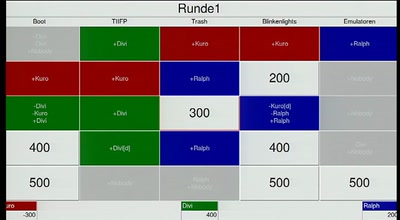
134 min
Hacker Jeopardy (english translation)
Number guessing for geeks

50 min
Data Analysis in Terabit Ethernet Traffic
Solutions for monitoring and lawful interception within a…

63 min
Spinning the electronic Wheel
Still the bicycles for the 21th century

59 min
Safety on the Open Sea
Safe navigation with the aid of an open sea chart.

41 min
Wikileaks und mehr
Eine Whistleblowerperspektive auf Leaking-Plattformen

62 min
Eins, zwei, drei - alle sind dabei
Von der Volkszählung zum Bundesmelderegister

62 min
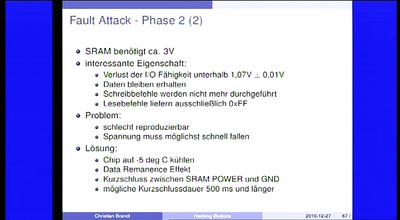
I Control Your Code
Attack Vectors Through the Eyes of Software-based Fault…

60 min
Von Zensursula über Censilia hin zum Kindernet
Jahresrückblick rund um Internet-Sperren,…

52 min
Adventures in Mapping Afghanistan Elections
The story of 3 Ushahidi mapping and reporting projects.

83 min
Fnord-Jahresrückblick 2010 (english translation)
von Atomausstieg bis Zwangsintegration
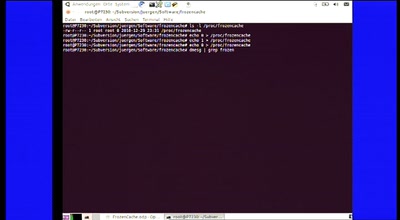
55 min
FrozenCache
Mitigating cold-boot attacks for Full-Disk-Encryption…

41 min
Digitale Spaltung per Gesetz
Das Internet und geschaffene soziale Ungleichheit im Alltag…

25 min
SIP home gateways under fire
Source routing attacks applied to SIP
60 min
Three jobs that journalists will do in 2050
Why future media may be more powerful (and more subversive)…
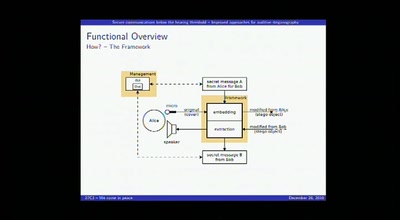
57 min
Secure communications below the hearing threshold
Improved approaches for auditive steganography
59 min
International Cyber Jurisdiction
Kill Switching” Cyberspace, Cyber Criminal Prosecution &…
121 min
Lightning Talks - Day 4
where is my community?

65 min
Zero-sized heap allocations vulnerability analysis
Applications of theorem proving for securing the windows…

56 min
IMMI, from concept to reality
The Icelandic Modern Media Initiative and our need for a…
60 min
Data Retention in the EU five years after the Directive
Why the time is now to get active

72 min
Lightning Talks - Day 3
where is my community?

47 min
From robot to robot
Restoring creativity in school pupils using robotics
49 min
Lightning Talks - Day 2
4 minutes of fame

55 min
Copyright Enforcement Vs. Freedoms
ACTA, IPRED3 and other upcoming battles of the crusade…
30 min