Search for "Benks"
prev
next
32 min
Augmenting the Human Mind

34 min
How the reputation economy is creating data-driven…

28 min
or how we learned to stop worrying and love the NSA

37 min
How cooperative online structures can facilitate…

60 min
Decentralizing semiconductor manufacturing

30 min
A tale of fault attacks on DRAM and attacks on CPU caches

46 min
Analyzing & Breaking Exploit Mitigations and Secure Random…

60 min
You have a tracking device in your pocket

44 min
Pragmatic Advice for Security Researchers
33 min
A view into technology on the other side of the world
59 min
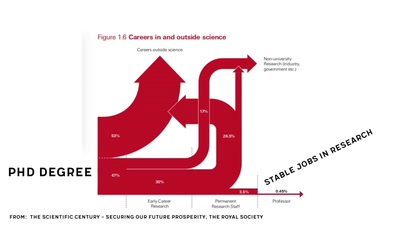
Let's understand how the scientific system works

64 min
Dissecting a Modern Wireless Network for the Internet of…

49 min
How to turn your KVM into a raging key-logging monster
60 min
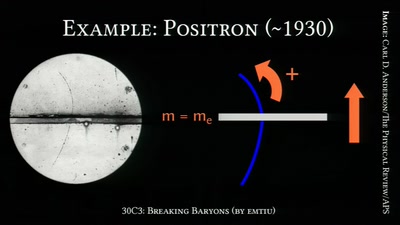
On the Awesomeness of Particle Accelerators and Colliders

61 min
... or how we battle the daemons of memory safety

61 min
The future does not look much brighter than ten years ago.…
prev
next









