Search for "see-base" returned 1773 results

60 min
On the insecure nature of turbine control systems in power generation
A security study of turbine control systems in power…

26 min
Humans as software extensions
Will You Be My Plugin?

60 min
The rise and fall of Internet voting in Norway
Evaluating a complex cryptographic implementation

54 min
How hackers grind an MMORPG: by taking it apart!
An introduction to reverse engineering network protocols
37 min
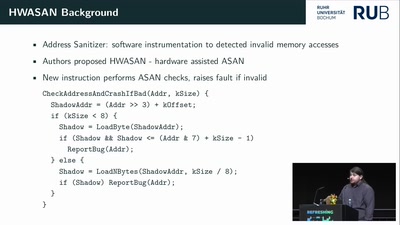
Inside the AMD Microcode ROM
(Ab)Using AMD Microcode for fun and security
38 min
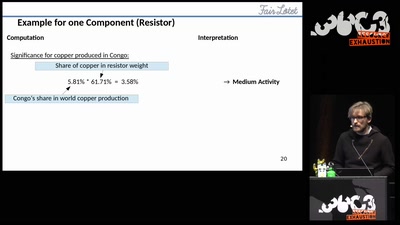
Fairtronics
A Tool for Analyzing the Fairness of Electronic Devices

64 min
Source Code and Cross-Domain Authorship Attribution
The Role of Stylometry in Privacy
39 min
Transmission Control Protocol
TCP/IP basics

33 min
Retail Surveillance / Retail Countersurveillance
50 most unwanted retail surveillance technologies / 50 most…

44 min
Disclosure DOs, Disclosure DON'Ts
Pragmatic Advice for Security Researchers
54 min