Search for "floX"
prev
next
56 min
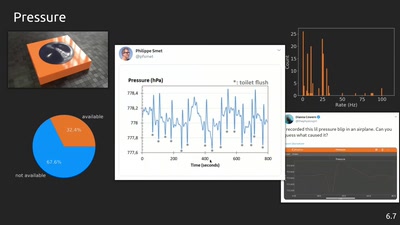
An open source project for education, research and tinkering

58 min
How to do things with words
43 min
Datenschutz-Mythen aus 5 Jahren DS-GVO

45 min
Digital Identity Systems in the EU & around the world

57 min
An introduction into reverse-engineering x86 microcode and…
64 min
Warum wir zivilen Ungehorsam und Subversion mehr brauchen…

40 min
Call the frontdoor to install your backdoors
61 min
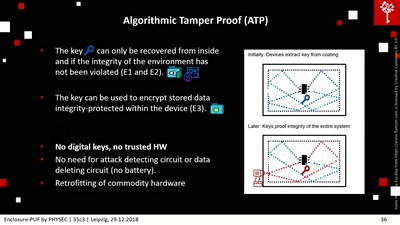
Tamper Proofing Commodity Hardware and other Applications

58 min
Intimiditation surveillance and other tactics observed and…
65 min
Take a deep breath into pollution trickery

61 min
A proposal for secure computing in an age where we cannot…

58 min
Die Krise der Politik ist die Krise der Bilder

58 min
From the Outside Looking In
prev
next









