56 min
Is implementation the enemy of design?
61 min
Everything about the C64 in 64 Minutes

61 min
Creating a rogue CA Certificate

61 min
Essentielles Grundwissen für alle, die nichts zu verbergen…

61 min
Bestandsaufnahme und Auswirkungen
94 min
Oder: worüber wir nächstes Jahr lachen werden
66 min
The Digital Enhanced Cordless Telecommunications standard
58 min
Recovering keys and other secrets after power off

76 min
Breaking Remote Keyless Entry Systems with Power Analysis
50 min
PowerLineCommunications has now their open source tool
56 min
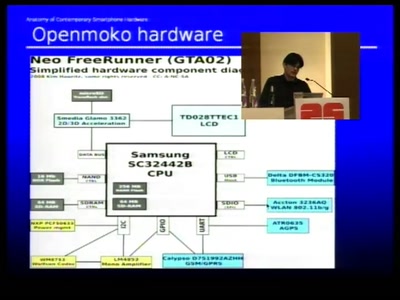
Dissecting contemporary cellphone hardware
58 min
Pwning Apple's Mobile Internet Device

65 min
Behind the scenes of the new light installation

44 min
Building an anonymous Internet within the Internet

82 min
First look at the security of NFC mobile phones
30 min
Accepting the Partial Disclosure Challenge
63 min
Overview of Current Keylogger Threats
46 min
Turning data into line noise and back

62 min
Past, present, and future

50 min
Open source BIOS replacement with a radical approach to…

58 min
Tampering the Tamper-Proof
35 min
A clever or ingenious device or expedient; adroit…

61 min
Not your mother's XSS bugs
63 min
Symbian Exploit and Shellcode Development

48 min
Reverse Engineering von 3D-Dateiformaten

48 min
Hide and Seek in A. Flash

92 min
Or: about what we will laugh next year

38 min
How to get useable information out of your honeypot