Search for "Bea" returned 6100 results
31 min
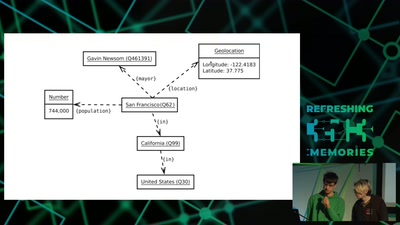
The Zcash anonymous cryptocurrency
or zero-knowledge succinct non-interactive arguments of…

39 min
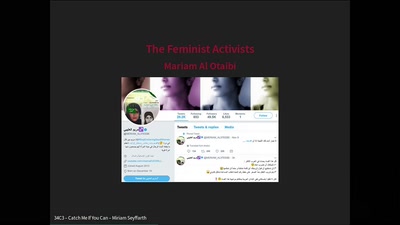
ID Cards in China: Your Worst Nightmare
In China Your ID Card Knows Everything

63 min
The Global Assassination Grid
The Infrastructure and People behind Drone Killings

60 min
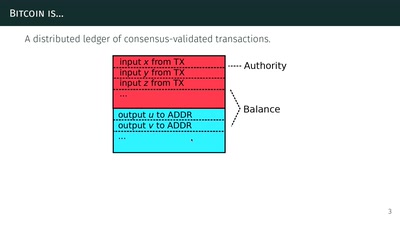
Why is GPG "damn near unusable"?
An overview of usable security research

27 min
Italy's surveillance toolbox
Research on Monitoring Italian Government Surveillance…

30 min
In Search of Evidence-Based IT-Security
IT security is largely a science-free field. This needs to…

30 min
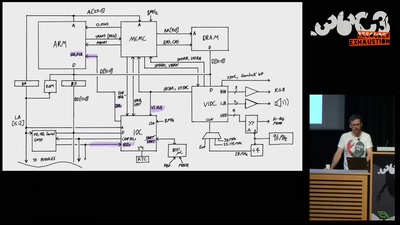
apertus° AXIOM
The first Open Source Cinema Camera
58 min
The Ultimate Acorn Archimedes talk
Everything about the Archimedes computer (with zero…

30 min
Information Control and Strategic Violence
How governments use censorship and surveillance as part of…
41 min
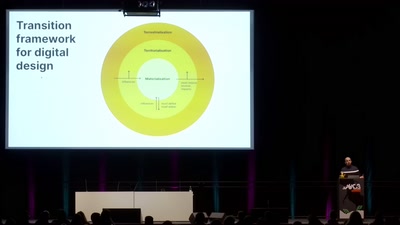
Framing digital industry into planetary limits and transition policies
The environmental costs of digital industry and pathways to…

58 min
Baseband Exploitation in 2013
Hexagon challenges

46 min
SELECT code_execution FROM * USING SQLite;
--Gaining code execution using a malicious SQLite database

59 min
Pointing Fingers at 'The Media'
The Bundestagswahl 2017 and Rise of the AfD
60 min
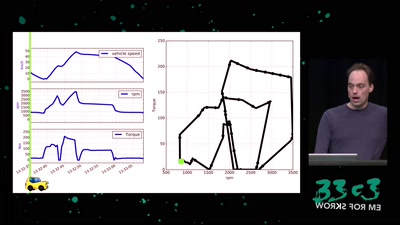
Software Defined Emissions
A hacker’s review of Dieselgate
62 min