Search for "tim" returned 6233 results

60 min
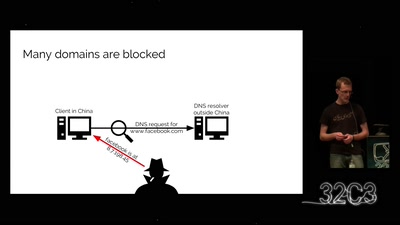
Why is GPG "damn near unusable"?
An overview of usable security research
60 min
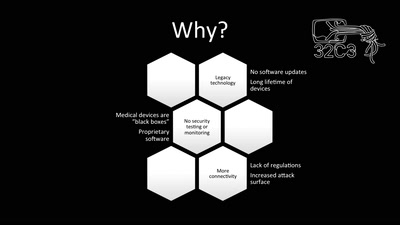
Unpatchable
Living with a vulnerable implanted device

62 min
Corporate surveillance, digital tracking, big data & privacy
How thousands of companies are profiling, categorizing,…

36 min
What I Learned from Loab: AI as a creative adversary
The artist behind the viral cryptid "Loab" reflects on her…
29 min
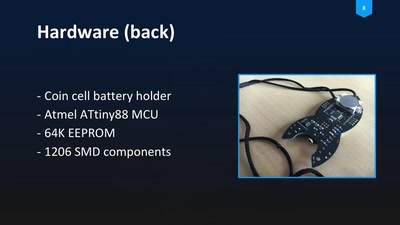
Blinkenrocket!
How to make a community project fly
55 min
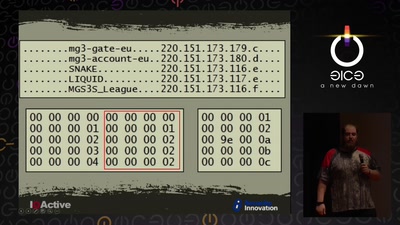
Cyber Necromancy
Reverse Engineering Dead Protocols

54 min
How hackers grind an MMORPG: by taking it apart!
An introduction to reverse engineering network protocols

49 min
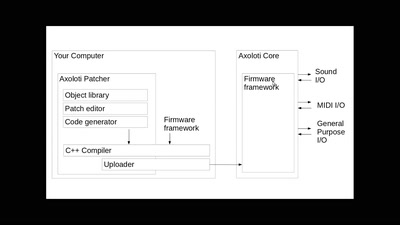
Open Source Firmware
Eine Liebesgeschichte

59 min
Hardsploit: A Metasploit-like tool for hardware hacking
A complete toolbox for IoT security

30 min
Syrian Archive
Preserving documentation of human rights violations

30 min
Science is broken
How much can we trust science in light failed replications,…

61 min