Search for "floX"
prev
next

63 min
how the EU was hypnotised that the NSA did not exist

60 min
A gentle introduction to post-quantum cryptography

46 min
--Gaining code execution using a malicious SQLite database
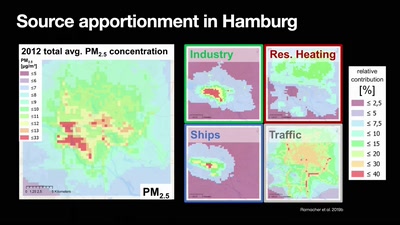
61 min
a journey from emissions to exposure

56 min
Hacking the most secure handheld console
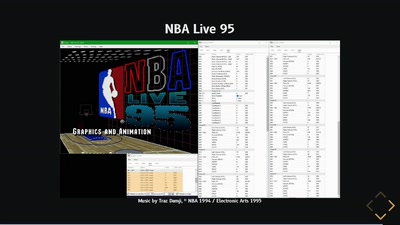
59 min
The hardware behind the music of Super Mario World, Chrono…

60 min
Autonomous flying vehicles, where are we and where are we…
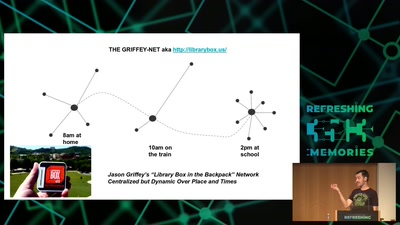
60 min
Integrating nearby and offline connectivity with the…

60 min
A semantics based approach
91 min
From Unanimity to Anonymity
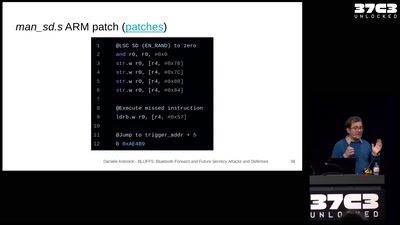
59 min
Breaking and fixing the Bluetooth standard. One More Time.

57 min
From DEFCON to the DARPA Cyber Grand Challenge

61 min
An Artificial Intelligence exploration into the creation of…
prev
next






