Search for person "Ilja Gerhardt" returned 14 results
39 min
Fuzzing the TCP/IP stack
beyond the trivial
58 min
Are all BSDs created equally?
A survey of BSD kernel vulnerabilities.

60 min
Windows drivers attack surface
some 'new' insights
61 min
X Security
It's worse than it looks
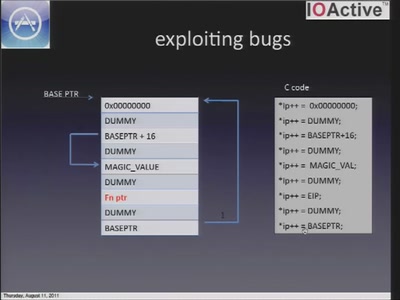
51 min
iOS application security
A look at the security of 3rd party iOS applications
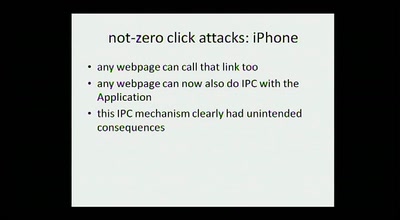
73 min
hacking smart phones
expanding the attack surface and then some

46 min