47 min
Adorno, Wilson und Diskordianismus

51 min
Illegal Art & Religious Bricolage

72 min
Oder: worüber wir nächstes Jahr lachen werden

54 min
Zivilrechtliche und strafrechtliche Haftung

68 min
How VMware, VirtualPC and Parallels actually work

60 min
Blogs, flickr, etc: warum machen wir es ihnen so einfach?

61 min
Wir helfen Euch, die Fnords zu sehen

53 min
How to find, invade and kill botnets automated and…

61 min
Better Living Through Inventing

63 min
Mandatory Access Control und TPM in Xen

53 min
Eine kulturanthropologische Untersuchung

61 min
Causes, Attacks and Countermeasures

66 min
The Role of Podcasting in Critical and Investigative…

57 min
An overview on design and generation of safe and reliable…

46 min
Finding exploitable vulnerabilities in binaries

58 min
Cross-layer optimization strategies for long-range IEEE…
52 min
How to start analyzing blackboxes
36 min
Grundlagen der Visualisierung und wie man mit…

71 min
Durchsuchung, Beschlagnahme, Vernehmung - Strategien für…

71 min
Experiences and lessons learned with the Payment Card…

52 min
radio politics in the USA and Germany in the first half of…
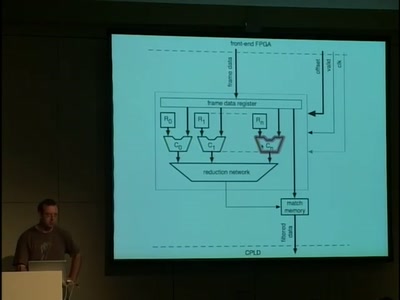
52 min
Hacking a 10 Gigabit Intrusion detection and prevention…

48 min
How the DVB project is locking down TV standards and…
58 min
How to build a complete FPGA-based DVB-T transmitter

46 min
Ein Erfahrungsbericht aus Malawi

107 min
The one and only hacker quizshow

60 min
Attacks, Defences and Public Policy Issues...

60 min
Investigating large-scale Internet content filtering

49 min
How to discover additional knowledge in the AOL query logs

54 min
An analysis of Apple's encrypted disk storage system

51 min
Werkzeuge und Vorgehen der STASI
62 min
Status Quo and Future Issues
53 min
Next generation vulnerabilities in 2.0 Web Applications

63 min
The Accessibility of Technology as an Addendum to…

79 min
Free RFID reader and emulator

53 min
The use of fuzzing in the corporate world over the years…
64 min
Wie trackt man automatisch sich bewegende Objekte?

56 min
Neue Entwicklungen beim ePass

62 min
The future and security of communicating vehicles

45 min
Any Technology Sufficiently Advanced is Indistinguishable…

45 min
"First we take Manhattan, then we take Berlin..."

51 min
Der Stand der Auseinandersetzung zwischen Discordiern und…

49 min
Wie funktioniert TCP mit 2kb RAM?

62 min
Erhellendes aus Philosophie und Soziologie zur Klärung des…

62 min
Cross Site Scripting and Client Side Web Services

97 min
EFF staffers answer your questions!

95 min
by anatomizing Linux' CPRNG
56 min
How we built ours - How you can build yours

50 min
Xbox 360, Playstation 3, Wii

62 min
Hot or Not: Defeating anonymity by monitoring clock skew to…

55 min
Pixel Fuzzing and the Bioinformatic Bindiff

87 min
Design of a blocking-resistant anonymity system

34 min
XMPP ist viel mehr als nur Instant Messaging

65 min
Functional body modification

78 min
Challenges in detecting system compromises and why we’re so…

45 min
Techniques and best practices to securely code your network…

60 min
Hardware Hacks and Cracks with FPGAs

59 min
Ein Überblick über die Aktivitäten des Clubs 2006

69 min
Encrypting (GSM) mobile phone calls over VPN with an…

56 min
Using the power of creative commons to create an…

58 min
The state and future of the World of Warcraft

47 min
A short look at my pet project implementation

54 min
Ist nicht jedes Passwort eine Manifestation des Mißtrauens?

62 min
Challenges of Organizing a Foundation for Hackers in the USA

54 min
Take a lot of Perl, add some OpenSSL, sprinkle it with a…

45 min
How to recognize trance coded communication patterns

52 min
Eine Lesung aus dem Buch "Schwarzbuch Datenschutz"

76 min
Sector-Oriented Analysis of the Potential Impact and…
57 min
State Authorities' Access to Sensitive Information
47 min
How bad security decisions can ruin a debit card design

64 min
Praktische Auswirkungen des neuen Strafrechtes, das in…

53 min
Busting Myths about Why Women Can't Be Technical

44 min
From tools, to tricks, to projects: build a translation…

135 min
Realtime in-building location tracking at the 23C3

64 min
Opening Ceremony and Keynote

58 min
Auch für Computer? - Nicht beim Go!

61 min
Ethereal^W Wireshark without remote exploits - a proof of…
63 min
Technische Mittel und soziale Aspekte des "Tracking &…

43 min
Firmware reverse-engineering tactics

98 min
How The Tech Culture Can Maintain Relevance In The 21st…

46 min
The Million Eyeball Principle and forkbombs
61 min
Die Zitierfähigkeit von Wiki-Wissen

48 min
A critical approach to the notion of gift economy within…
51 min
Ein audiovisuelles Live-Feature

68 min
News and Perspectives on Implementation and Opposition
50 min
Autonomous flying vehicles

138 min
The story of the dutch campaign against black-box voting to…

60 min
Kann ich dir ein Bier ausgeben?

61 min
An Overview Free and Open Source Software efforts and…

63 min
The 7 Laws of Identity and the Identity Metasystem

50 min
Eine Einführung in die neue, dynamische Sprache für das…
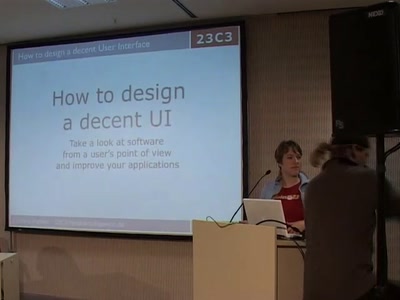
57 min
Take a look at software from a user's point of view and…
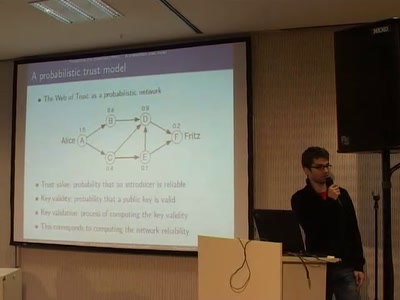
55 min
A new way of evaluating a PGP web of trust by using a…