Search for "John" returned 1046 results
55 min
The good, the strange and the ugly in 2018 art &tech
On art, AI, hormones hacking and other prospects of a…

63 min
Reproducible Builds
Moving Beyond Single Points of Failure for Software…
65 min
Rocket science – how hard can it be?
First steps into space with sounding rockets

32 min
Fuck Dutch mass-surveillance: let's have a referendum!
Forcing the Netherlands to publicly debate privacy and the…

63 min
Building Custom Pinball Machines
What you need and how it works. An experiences report

51 min
Virtual Secure Boot
Secure Boot support in qemu, kvm and ovmf.

58 min
Switches Get Stitches
Industrial System Ownership

41 min
NGI Zero: A treasure trove of IT innovation
Resilient. Trustworthy. Sustainably Open.

44 min
ASLR on the line
Practical cache attacks on the MMU

31 min
PUFs, protection, privacy, PRNGs
an overview of physically unclonable functions
60 min
Das Zahnrad aus Fleisch
Expeditionen ins Kommentierreich

60 min
Attacking end-to-end email encryption
Efail, other attacks and lessons learned.

63 min
Reconstructing narratives
transparency in the service of justice

66 min
Mit, gegen oder jenseits von Politik?
Eine Reflexion über den paradoxen anarchistischen…
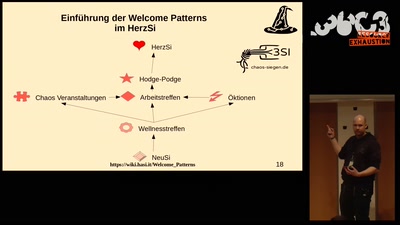
40 min
Welcome Pattern - Theorie und Praxis
(Eine Gemeinschaftsproduktion der Haecksen, der…

60 min
Intel Management Engine deep dive
Understanding the ME at the OS and hardware level
60 min
Lifting the Fog on Red Star OS
A deep dive into the surveillance features of North Korea's…

55 min
Vehicle immobilization revisited
Uncovering and assessing a second authentication mechanism…

60 min