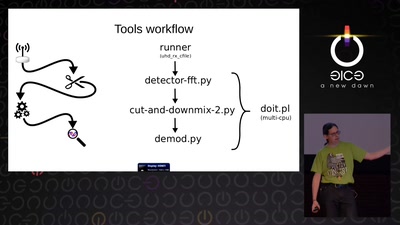
Search for "Bre" returned 5536 results

46 min
Taking a scalpel to QNX
Analyzing & Breaking Exploit Mitigations and Secure Random…

57 min
A Dozen Years of Shellphish
From DEFCON to the DARPA Cyber Grand Challenge

61 min
Net Neutrality in Europe
alea iacta est

59 min
Hardsploit: A Metasploit-like tool for hardware hacking
A complete toolbox for IoT security
33 min
The Transhumanist Paradox
Deciding between technological utopias in a liberal state

38 min
Schnaps Hacking
from apple to schnaps -- a complete diy-toolchain

58 min
When hardware must „just work“
An inside look at x86 CPU design

33 min
institutions for Resolution Disputes
Rosa Menkman investigates video compression, feedback, and…

60 min
Quantum Cryptography
from key distribution to position-based cryptography
66 min
31C3 Keynote
A New Dawn

62 min
Calafou, postcapitalist ecoindustrial community
Building a space for grassroots sustainable technology…

51 min
Virtual Secure Boot
Secure Boot support in qemu, kvm and ovmf.
61 min