Search for "max" returned 4567 results

58 min
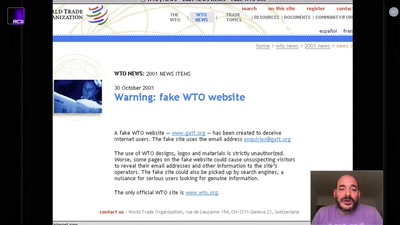
Thwarting Evil Maid Attacks
Physically Unclonable Functions for Hardware Tamper…

51 min
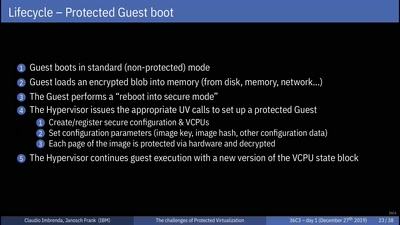
Virtual Secure Boot
Secure Boot support in qemu, kvm and ovmf.

67 min
The Maker movement meets patent law
How many windows are open in the patent fortress
23 min
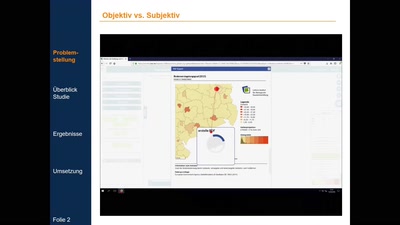
Ich sehe was, was Du nicht siehst
Bewertung der Usability freier Web-GIS am Beispiel einer…

60 min
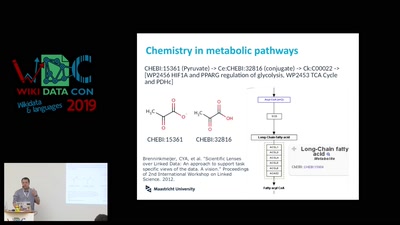
APT Reports and OPSEC Evolution, or: These are not the APT reports you are looking for
How advanced threat actors learn and change with innovation…
62 min
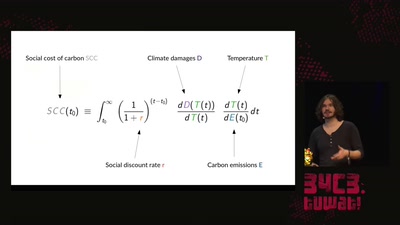
A hacker's guide to Climate Change - What do we know and how do we know it?
An introduction to the basics of climate research and what…

54 min
AMD x86 SMU firmware analysis
Do you care about Matroshka processors?

40 min
The Great Escape of ESXi
Breaking Out of a Sandboxed Virtual Machine

60 min
Quantum Cryptography
from key distribution to position-based cryptography

25 min
Regulating Autonomous Weapons
The time travelling android isn’t even our biggest problem
39 min
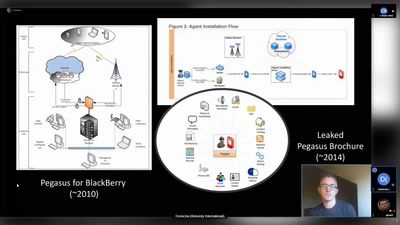
The Eye on the Nile
Egypt's Civil Society Under Attack

46 min