Search for "Theo Voss" returned 433 results

60 min
Everything you always wanted to know about Certificate Transparency
(but were afraid to ask)
35 min
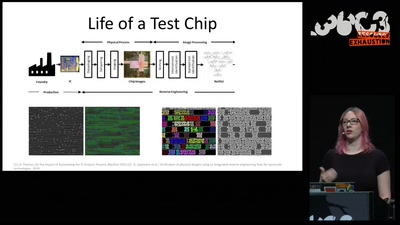
Understanding millions of gates
Introduction to IC reverse engineering for…

64 min
We only have one earth
A case for expansionistic space policy

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities
38 min
Policing the Romantic Crowd
Velocipedes and Face Recognition

64 min
Technical aspects of the surveillance in and around the Ecuadorian embassy in London
Details about the man hunt for Julian Assange and Wikileaks

59 min
TamaGo - bare metal Go framework for ARM SoCs.
Reducing the attack surface with pure embedded Go.

58 min
Thwarting Evil Maid Attacks
Physically Unclonable Functions for Hardware Tamper…

60 min
Open Source is Insufficient to Solve Trust Problems in Hardware
How Betrusted Aims to Close the Hardware TOCTOU Gap

35 min
Harry Potter and the Not-So-Smart Proxy War
Taking a look at a covert CIA virtual fencing solution

59 min
Visiting The Bear Den
A Journey in the Land of (Cyber-)Espionage
60 min
Opening Closed Systems with GlitchKit
'Liberating' Firmware from Closed Devices with Open Source…

55 min
Graphs, Drones & Phones
The role of social-graphs for Drones in the War on Terror.

41 min
Extracting keys from FPGAs, OTP Tokens and Door Locks
Side-Channel (and other) Attacks in Practice

49 min
Dissecting VoLTE
Exploiting Free Data Channels and Security Problems

50 min
Heimlich-Manöver
Best of Informationsfreiheit & Gefangenenbefreiung
60 min
Prediction and Control
Watching Algorithms
55 min