Search for "wose" returned 848 results

60 min
Attacking end-to-end email encryption
Efail, other attacks and lessons learned.

58 min
How risky is the software you use?
CITL: Quantitative, Comparable Software Risk Reporting

40 min
What is this? A machine learning model for ants?
How to shrink deep learning models, and why you would want…

32 min
History and implications of DRM
From tractors to Web standards

36 min
Apple's iPhone 15: Under the C
Hardware hacking tooling for the new iPhone generation
57 min
Hello World!
How to make art after Snowden?

63 min
The Cloud Conspiracy 2008-2014
how the EU was hypnotised that the NSA did not exist
44 min
Why Nobody cares, and only You can save the World
Technology, Intuitions & Moral Expertise

56 min
Viva la Vita Vida
Hacking the most secure handheld console
63 min
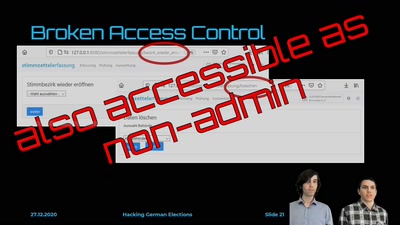
Hacking German Elections
Insecure Electronic Vote Counting - How It Returned and Why…

60 min
Building a high throughput low-latency PCIe based SDR
Lessons learnt implementing PCIe on FPGA for XTRX Software…

38 min