41 min
Nym Anonymous Authentication Credentials
42 min
Or how to become your own ISP
46 min
...or the 37th floor of a Hotel
30 min
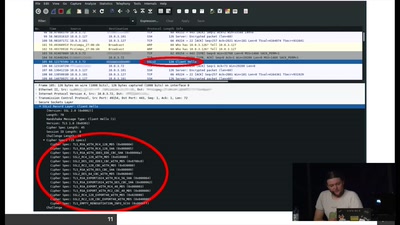
Über die (Un-)Sicherheit eines Bezahlsystems
46 min
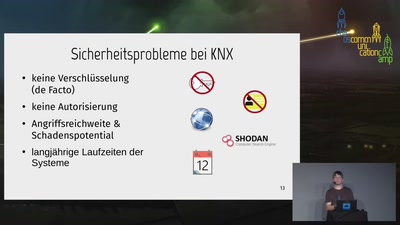
Was kann man noch retten, wenn langlebigen Strukturen…
43 min
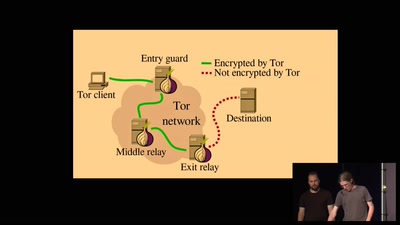
The Road to Mobile Tor and Improved Censorship Circumvention

40 min
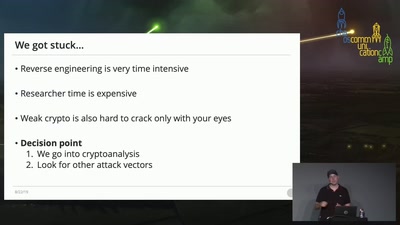
Owning machines through relaying and delegation
45 min
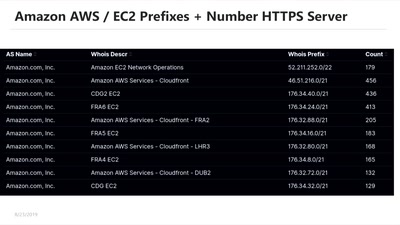
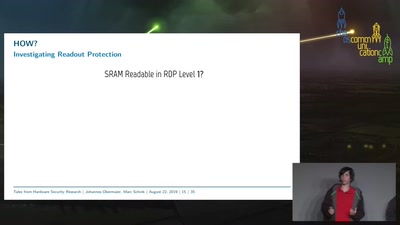
From Research over Vulnerability Discovery to Public…

46 min
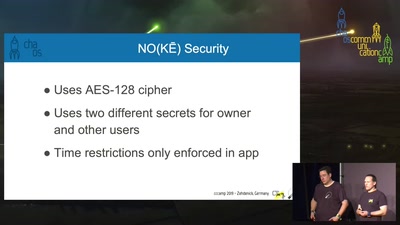
Redesigning NoScript’s UX

49 min
secure your apps and servers through continuous integration

43 min
how to make NetBSD a better software for you and me

44 min
Retiring the BSD Socket API
41 min
A beginner-friendly guide to network segmentation for…
43 min
The dilemma of DNS privacy protocols
43 min
Exploiting and protecting containers with a few lines of…