In this talk we will present how intermediate code transformations can be used to obfuscate code and the advantadges and limitations they introduce. We will also brielfy discuss some techniques that could help detect and reverse code obfuscated in such ways.
Despite their limitations, intermediate languages like LLVM-IR provide the best way to write code transformations that work well for all the input and output languages supported by the compiler framework.
Usually, this is used to write optimization passes, but nothing prevents you from using them to make the resulting code less inteligible to an external reader.
This talk will focus on how different obfuscation techniques can be implemented and used as such passes and what are the limitations that may make implementing, for example, an unpacker a bit harder.
We will also cover how some of these techniques can be reversed (specially when perfoming comparative analysis).
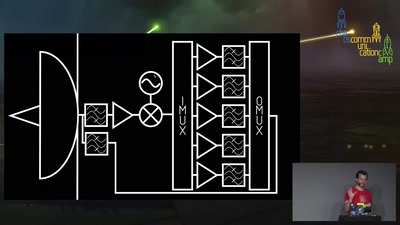
Keep in mind that although LO started as a way to provide a way to deterministically increase variability in generated code and make finding out the patched flaws harder, many of it's techniques like code flattening or constant expansions are also used by other users of obfuscated code, for example malware.
Download
Video
These files contain multiple languages.
This Talk was translated into multiple languages. The files available for download contain all languages as separate audio-tracks. Most desktop video players allow you to choose between them.
Please look for "audio tracks" in your desktop video player.