44 min
Console Hacking 2010
PS3 Epic Fail

51 min
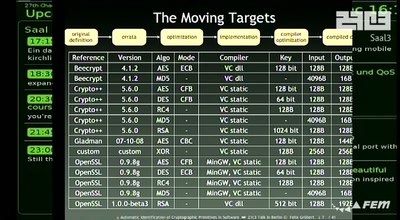
Reverse Engineering the MOS 6502 CPU
3510 transistors in 60 minutes
57 min
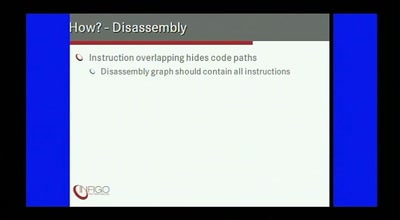
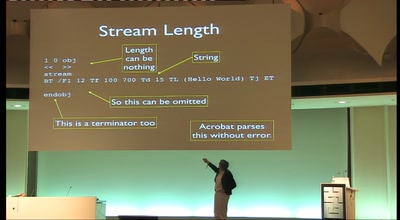
OMG WTF PDF
What you didn't know about Acrobat

60 min
"Die gesamte Technik ist sicher"
Besitz und Wissen: Relay-Angriffe auf den neuen…
39 min
Cybernetics for the Masses
implants, sensory extension and silicon - all for you!

56 min
JTAG/Serial/FLASH/PCB Embedded Reverse Engineering Tools and Techniques
a dump of simple tools for embedded analysis at many layers

61 min
Running your own GSM stack on a phone
Introducing Project OsmocomBB
58 min
Reverse Engineering a real-world RFID payment system
Corporations enabling citizens to print digital money

61 min
SMS-o-Death
From analyzing to attacking mobile phones on a large scale.
66 min
The Baseband Apocalypse
all your baseband are belong to us
63 min
Android geolocation using GSM network
"Where was Waldroid?"
57 min
Chip and PIN is Broken
Vulnerabilities in the EMV Protocol

58 min
Analyzing a modern cryptographic RFID system
HID iClass demystified
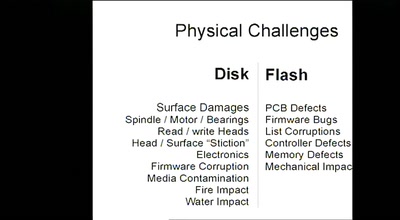
60 min
Data Recovery Techniques
Fun with Hard Drives

64 min
Defense is not dead
Why we will have more secure computers - tomorrow
47 min
The Hidden Nemesis
Backdooring Embedded Controllers
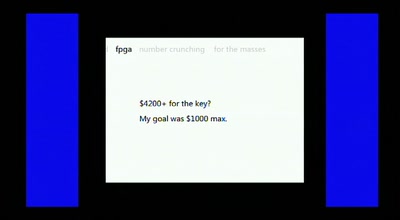
56 min
Distributed FPGA Number Crunching For The Masses
How we obtained the equivalent power of a Deep Crack for a…
73 min
hacking smart phones
expanding the attack surface and then some
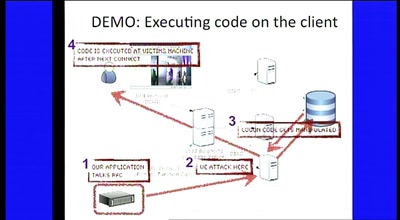
76 min
Rootkits and Trojans on Your SAP Landscape
SAP Security and the Enterprise

34 min
Lying To The Neighbours
Nasty effects with tracker-less BitTorrent
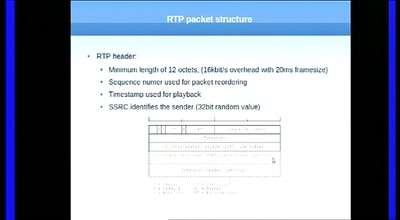
36 min
Having fun with RTP
„Who is speaking???“

59 min
Part-Time Scientists
One year of Rocket Science!
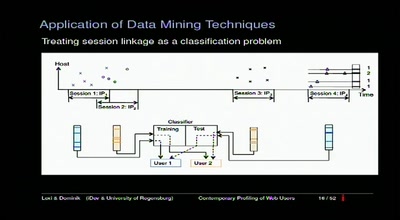
54 min
Contemporary Profiling of Web Users
On Using Anonymizers and Still Get Fucked

50 min
Data Analysis in Terabit Ethernet Traffic
Solutions for monitoring and lawful interception within a…

62 min
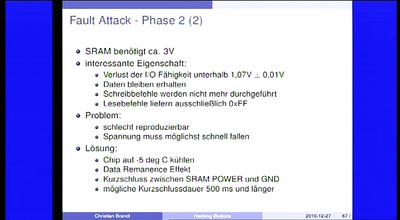
I Control Your Code
Attack Vectors Through the Eyes of Software-based Fault…
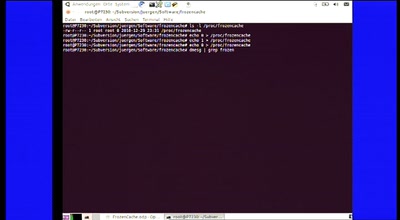
55 min
FrozenCache
Mitigating cold-boot attacks for Full-Disk-Encryption…

25 min
SIP home gateways under fire
Source routing attacks applied to SIP
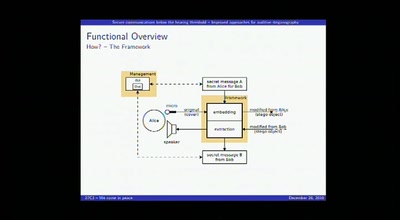
57 min
Secure communications below the hearing threshold
Improved approaches for auditive steganography

65 min