54 min
Vier Fäuste für ein Halleluja
Geschichten aus dem API-und Protokollkrieg von zwei…

57 min
SCCP hacking, attacking the SS7 & SIGTRAN applications one step further and mapping the…
Back to the good old Blue Box?

56 min
Blackbox JTAG Reverse Engineering
Discovering what the hardware architects try to hide from…
37 min
Reverse-Engineering DisplayLink devices
USB to DVI for Hackers
32 min
"Haste ma'n netblock?"
Layer 8 based IP Address hijacking in the end of the days…
71 min
Defending the Poor
Preventing Flash Exploits

70 min
coreboot: Adding support for a system near you
Working with the open source BIOS replacement and getting a…

51 min
Advanced microcontroller programming
Getting deeper into AVR programming
55 min
Building a Debugger
Open JTAG with Voltage Glitching
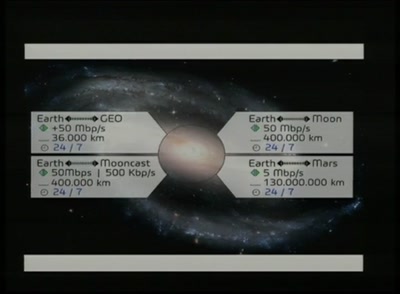
128 min
A part time scientists' perspective of getting to the moon
presenting the first German Team participating in the…
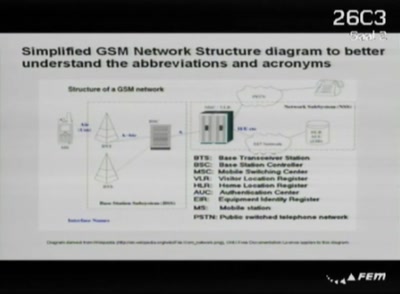
47 min
Playing with the GSM RF Interface
Doing tricks with a mobile phone

61 min
DECT (part II)
What has changed in DECT security after one year
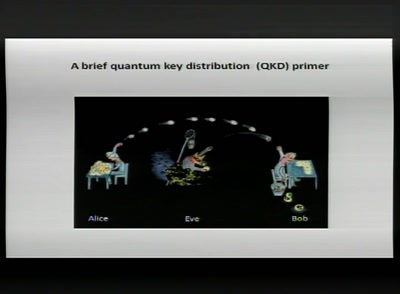
52 min
How you can build an eavesdropper for a quantum cryptosystem
hardware demo during the lecture
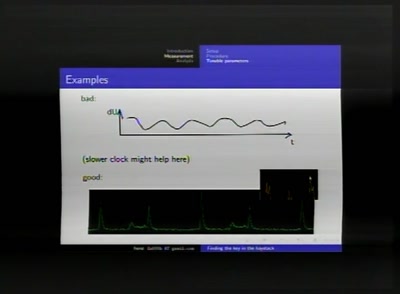
50 min
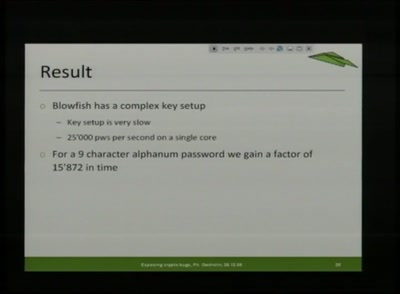
Finding the key in the haystack
A practical guide to Differential Power Analysis

40 min