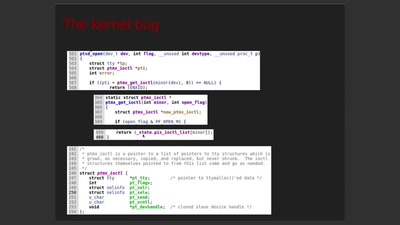
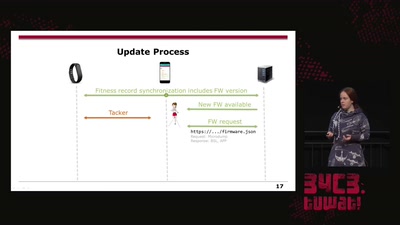
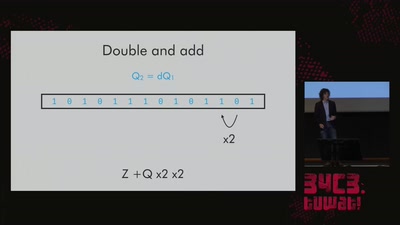
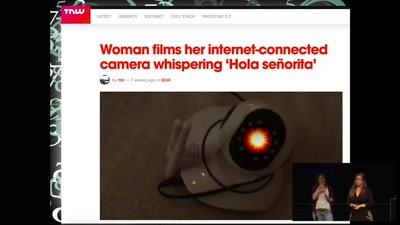
Trusted Execution Environments (TEEs), like those based on ARM TrustZone or Intel SGX, intend to provide a secure way to run code beyond the typical reach of a computer’s operating system.
However, when trusted and untrusted code runs on shared hardware, it opens the door to the same microarchitectural attacks that have been exploited for years. This talk provides an overview of these attacks as they have been applied to TEEs, and it additionally demonstrates how to mount these attacks on common TrustZone implementations. Finally, we identify new techniques which allow us to peer within TrustZone TEEs with greater resolution than ever before.
Download
Video
These files contain multiple languages.
This Talk was translated into multiple languages. The files available for download contain all languages as separate audio-tracks. Most desktop video players allow you to choose between them.
Please look for "audio tracks" in your desktop video player.