52 min
Ladeinfrastruktur für Elektroautos: Ausbau statt Sicherheit
Warum das Laden eines Elektroautos unsicher ist
56 min
Console Security - Switch
Homebrew on the Horizon

57 min
Everything you want to know about x86 microcode, but might have been afraid to ask
An introduction into reverse-engineering x86 microcode and…
22 min
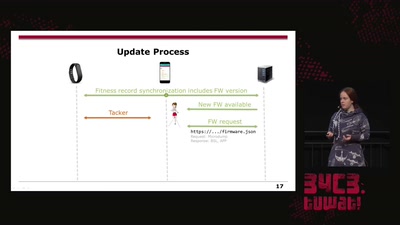
Doping your Fitbit
On Fitbit Firmware Modifications and Data Extraction

51 min
How to drift with any car
(without your mom yelling at you)
58 min
Are all BSDs created equally?
A survey of BSD kernel vulnerabilities.
45 min
SCADA - Gateway to (s)hell
Hacking industrial control gateways
31 min
DPRK Consumer Technology
Facts to fight lore

58 min
Decoding Contactless (Card) Payments
An Exploration of NFC Transactions and Explanation How…

56 min
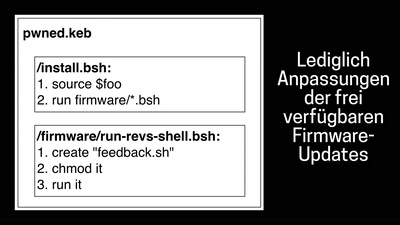
eMMC hacking, or: how I fixed long-dead Galaxy S3 phones
A journey on how to fix broken proprietary hardware by…
65 min
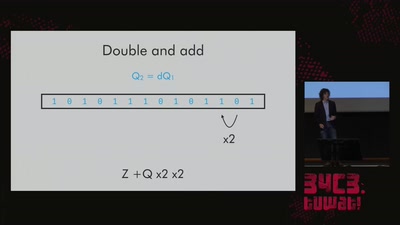
LatticeHacks
Fun with lattices in cryptography and cryptanalysis

60 min
Lets break modern binary code obfuscation
A semantics based approach

44 min
ASLR on the line
Practical cache attacks on the MMU

51 min
Uncovering vulnerabilities in Hoermann BiSecur
An AES encrypted radio system

49 min
Electromagnetic Threats for Information Security
Ways to Chaos in Digital and Analogue Electronics

59 min
We should share our secrets
Shamir secret sharing: How it works and how to implement it

46 min
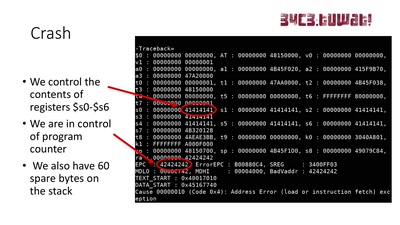
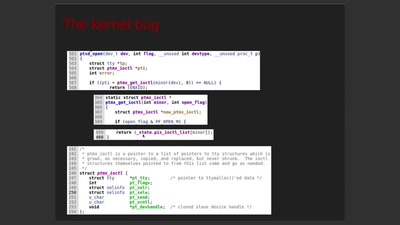
Taking a scalpel to QNX
Analyzing & Breaking Exploit Mitigations and Secure Random…

31 min