Search for "wose" returned 847 results

45 min
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache
40 min
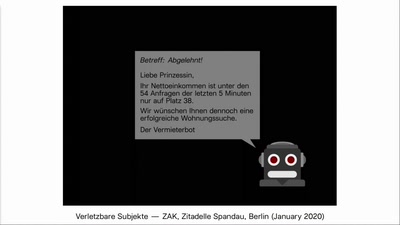
Wohnungsbot: An Automation-Drama in Three Acts
A media-art project which automates the search for flats in…
60 min
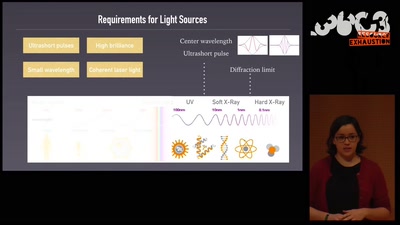
An ultrashort history of ultrafast imaging
Featuring the shortest movies and the largest lasers
56 min
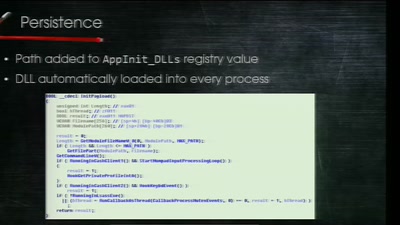
Electronic Bank Robberies
Stealing Money from ATMs with Malware

53 min
Million Dollar Dissidents and the Rest of Us
Uncovering Nation-State Mobile Espionage in the Wild

55 min
The DROWN Attack
Breaking TLS using SSLv2
61 min
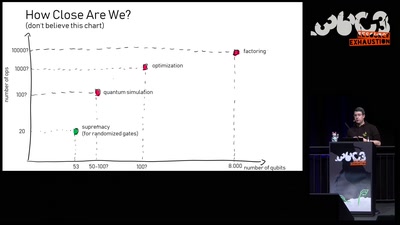
Quantum Computing: Are we there yet?
An introduction to quantum computing and a review of the…

42 min
Firmware Fat Camp
Embedded Security Using Binary Autotomy

51 min
Virtual Secure Boot
Secure Boot support in qemu, kvm and ovmf.

63 min
A look into the Mobile Messaging Black Box
A gentle introduction to mobile messaging and subsequent…

41 min
Extracting keys from FPGAs, OTP Tokens and Door Locks
Side-Channel (and other) Attacks in Practice

49 min
Dissecting VoLTE
Exploiting Free Data Channels and Security Problems
40 min
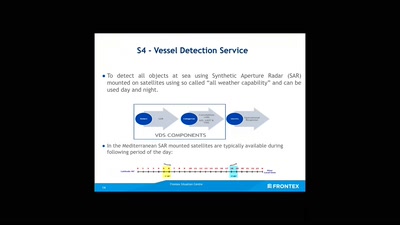
No roborders, no nation, or: smile for a European surveillance propagation
How an agency implements Fortress Europe by degrading…
59 min
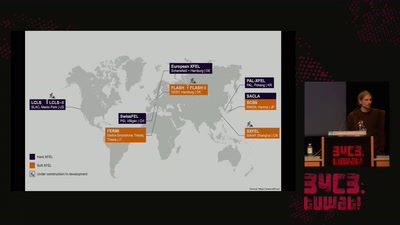
Free Electron Lasers
...or why we need 17 billion Volts to make a picture.
58 min
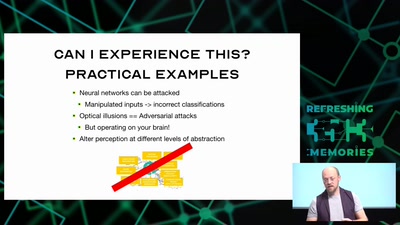
Hacking how we see
A way to fix lazy eye?

59 min
Memory Deduplication: The Curse that Keeps on Giving
A tale of 3 different memory deduplication based…

60 min
Concepts for global TSCM
getting out of surveillance state mode

58 min