Search for "Ike" returned 2691 results

58 min
Baseband Exploitation in 2013
Hexagon challenges

26 min
Humans as software extensions
Will You Be My Plugin?

60 min
Why is GPG "damn near unusable"?
An overview of usable security research

62 min
Bionic Ears
Introduction into State-of-the-Art Hearing Aid Technology

54 min
AMD x86 SMU firmware analysis
Do you care about Matroshka processors?

55 min
Revisiting SSL/TLS Implementations
New Bleichenbacher Side Channels and Attacks

58 min
Decoding Contactless (Card) Payments
An Exploration of NFC Transactions and Explanation How…
37 min
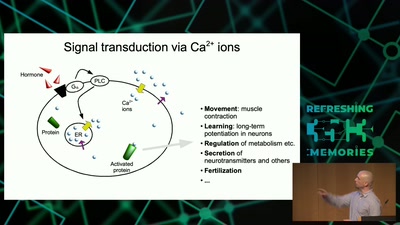
Information Biology - Investigating the information flow in living systems
From cells to dynamic models of biochemical pathways and …

39 min
Tales of old: untethering iOS 11
Spoiler: Apple is bad at patching

60 min
Profiling (In)justice
Disaggregating Data by Race and Ethnicity to Curb…
32 min
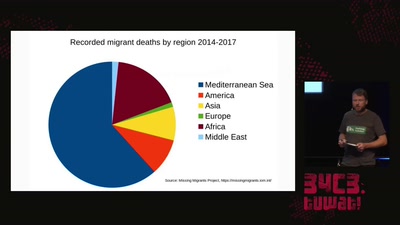
The seizure of the Iuventa
How search and rescue in the mediterranean was criminalized

32 min
Modern key distribution with ClaimChain
A decentralized Public Key Infrastructure that supports…

39 min
Web-based Cryptojacking in the Wild
When your browser is mining coins for other people
47 min
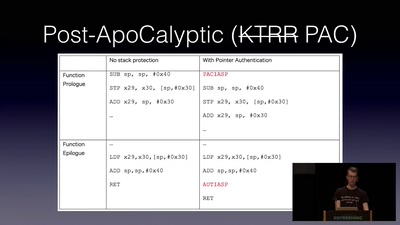
Jailbreaking iOS
From past to present

59 min