
45 min
When physical security depends on IT security
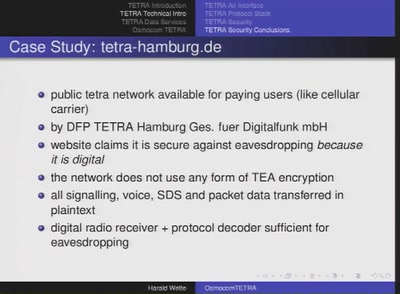
56 min
digital radio technology beyond GSM
40 min
A roundup of one the most advanced open hardware projects
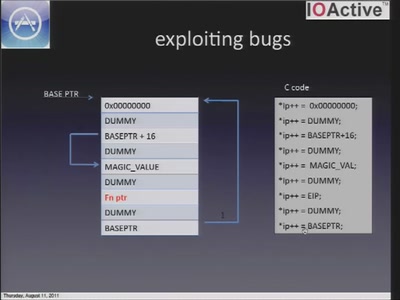
51 min
A look at the security of 3rd party iOS applications

55 min
Or: How I walked in and misbehaved
51 min
Wardriving phone networks
51 min
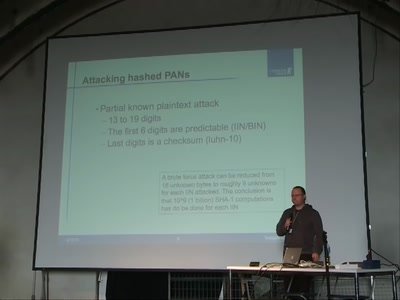
Attacks on common failures when encrypting credit card…
58 min
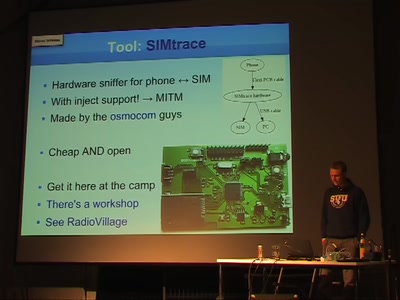
Some details about SIM cards







