51 min
Wie der Weg ins digitale Zuhause zum Spaziergang wird
61 min
Hacking the most popular cryptocurrency hardware wallets
46 min
Hacking your network likes it's 1980 again

39 min
Vom Fall der letzten Bastion biometrischer Systeme

61 min
"So sicher wie beim Online-Banking": Die elektronische…
32 min
A long way to a vibrant future
37 min
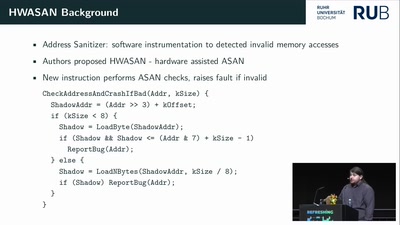
(Ab)Using AMD Microcode for fun and security

52 min
How I Learned to Stop Worrying and Love the Backdoor
38 min
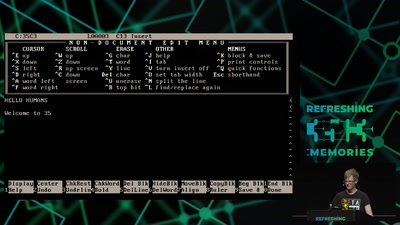
Explaining in detail just how those little COM files…

56 min
Hacking the most secure handheld console

60 min
Efail, other attacks and lessons learned.

54 min
Reliably finding bugs to escape the Chrome sandbox

36 min
Hardware implants in the supply-chain

61 min
why clearing memory is hard.

58 min
weaknesses in the encryption of solid state drives (SSDs)

57 min
A demystification of the exploit development lifecycle

60 min
Enforcing strong network segmentation, without anyone…

54 min
Unlocking God Mode on Linux
49 min
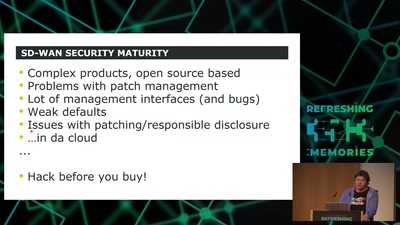
How to hack software defined network and keep your sanity?
35 min
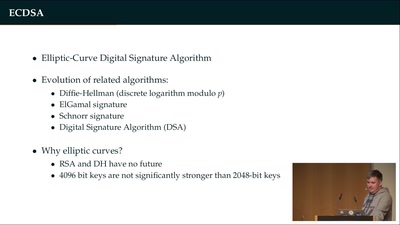
How (not) to protect private keys

39 min
When your browser is mining coins for other people
42 min
Hierarchical decentralized naming system used since 30 years

59 min
How I learned to stop worrying and love the backdoor
61 min
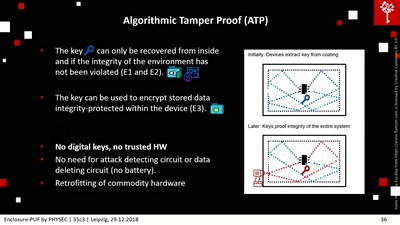
Tamper Proofing Commodity Hardware and other Applications