52 min
Warum das Laden eines Elektroautos unsicher ist

57 min
An introduction into reverse-engineering x86 microcode and…
22 min
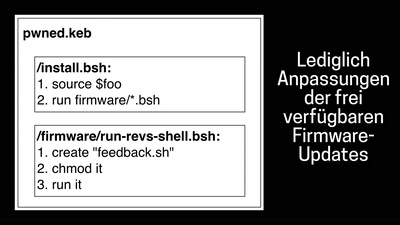
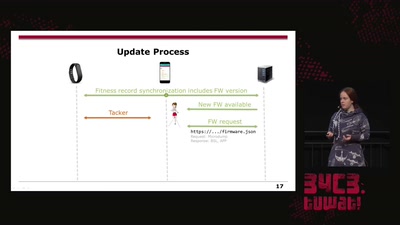
On Fitbit Firmware Modifications and Data Extraction

51 min
(without your mom yelling at you)
58 min
A survey of BSD kernel vulnerabilities.
45 min
Hacking industrial control gateways

58 min
An Exploration of NFC Transactions and Explanation How…
65 min
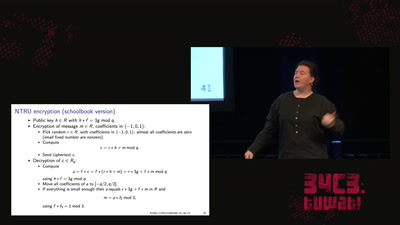
Fun with lattices in cryptography and cryptanalysis

56 min
A journey on how to fix broken proprietary hardware by…

60 min
A semantics based approach

60 min
A critical look on a new audio Format

44 min
Practical cache attacks on the MMU

55 min
Towards an open source binary firmware analysis framework

51 min
An AES encrypted radio system

49 min
Ways to Chaos in Digital and Analogue Electronics

59 min
Shamir secret sharing: How it works and how to implement it

46 min
Analyzing & Breaking Exploit Mitigations and Secure Random…

31 min
Hijacking debug components for embedded security