Search for "Pau Espin"
prev

37 min
Don't ask what you can do for TPMs, Ask what TPMs can do…

32 min
Automatic detection of key-reuse vulnerabilities
62 min
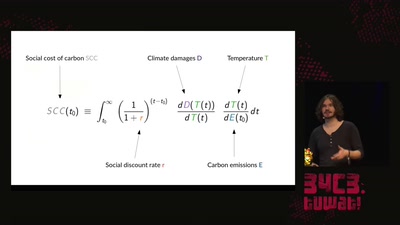
An introduction to the basics of climate research and what…

55 min
The role of social-graphs for Drones in the War on Terror.
prev



