Search for "Bea" returned 6098 results

39 min
The automobile as massive data gathering source and the consequences for individual…
The next big privacy heist

58 min
Switches Get Stitches
Industrial System Ownership
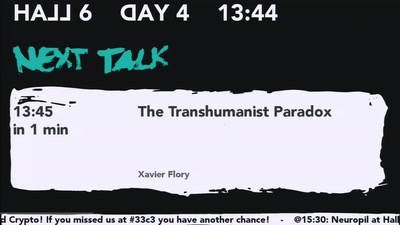
33 min
The Transhumanist Paradox
Deciding between technological utopias in a liberal state

56 min
Household, Totalitarianism and Cyberspace
Philosophical Perspectives on Privacy Drawing on the…

46 min
Taking a scalpel to QNX
Analyzing & Breaking Exploit Mitigations and Secure Random…
61 min
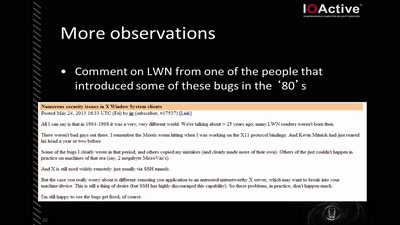
X Security
It's worse than it looks

38 min
Schnaps Hacking
from apple to schnaps -- a complete diy-toolchain

51 min
Wireless Drivers: Freedom considered harmful?
An OpenWrt perspective on the development of Linux 802.11…

57 min
A Dozen Years of Shellphish
From DEFCON to the DARPA Cyber Grand Challenge

61 min
Code Pointer Integrity
... or how we battle the daemons of memory safety

59 min
Fernvale: An Open Hardware and Software Platform, Based on the (nominally) Closed-Source…
A Lawful Method for Converting Closed IP into Open IP
59 min
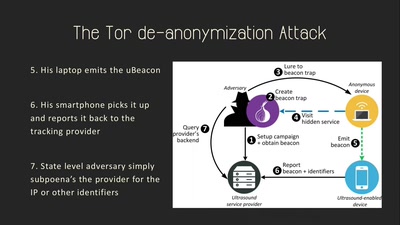
Talking Behind Your Back
On the Privacy & Security of the Ultrasound Tracking…
46 min
Making machines that make
rapid prototyping of digital fabrication and…

59 min
Hardsploit: A Metasploit-like tool for hardware hacking
A complete toolbox for IoT security
60 min
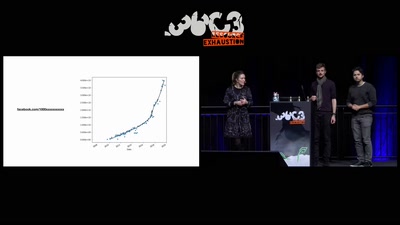
Inside the Fake Like Factories
How thousands of Facebook, You Tube and Instagram pages…

61 min