35 min
Taking a look at a covert CIA virtual fencing solution

37 min
Don't ask what you can do for TPMs, Ask what TPMs can do…

39 min
Spoiler: Apple is bad at patching

40 min
Breaking Out of a Sandboxed Virtual Machine
41 min
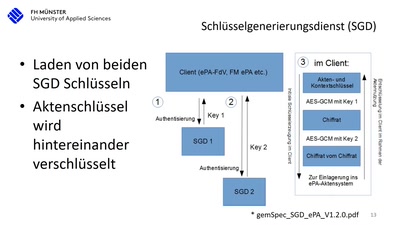
Die Realität beim Arztbesuch nach 15 Jahren Entwicklung…

43 min
Menschliche Faktoren der IT-Sicherheit

46 min
Exploring a new attack surface on the 3DS

46 min
--Gaining code execution using a malicious SQLite database

48 min
3 different RCE vulnerabilities on Ruckus Wireless access…
52 min
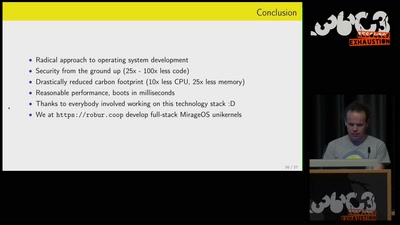
Reducing carbon footprint of network services with MirageOS…

53 min
An introduction without maths
55 min
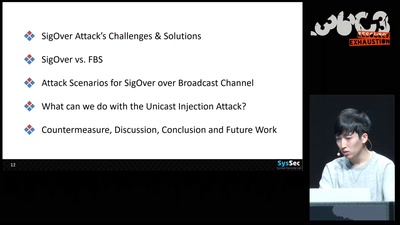
Signal overshadowing attack on LTE and its applications

55 min
Uncovering and assessing a second authentication mechanism…

55 min
Leaking Your Recent Memory Operations on Intel CPUs

58 min
Breaking PDF Encryption and PDF Signatures

59 min
Reducing the attack surface with pure embedded Go.

60 min
Understanding the ME at the OS and hardware level

60 min
A security study of turbine control systems in power…
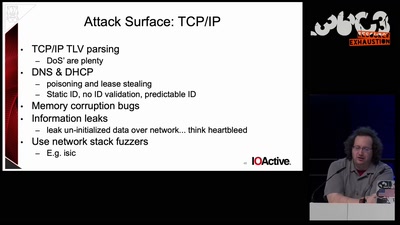
62 min
Auditing Boot Loaders by Example

63 min
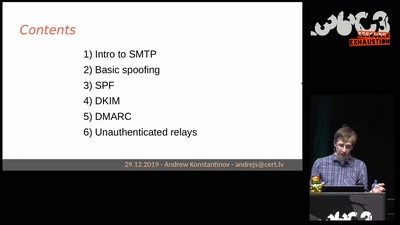
Können wir Software bauen, die nützlich /und/ unbedenklich…