22 min
Net-activism strategies against fake web companies
27 min
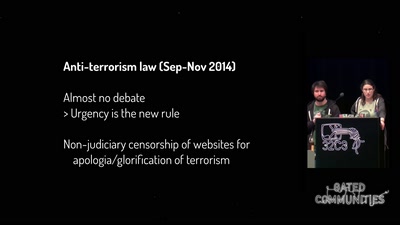
From the Bill on Intelligence to the State of Emergency
27 min
Hackers, I call thee to our Oceans!

28 min
One can create art and beauty with … pixels

29 min
Wireless Physical Layer Security & More...

30 min
The first Open Source Cinema Camera

30 min
How I failed to run an open source project

30 min
Journalism ♥ Computer Science

30 min
Visualizing WLAN Channel Usage on OpenWRT

30 min
A tale of fault attacks on DRAM and attacks on CPU caches

32 min
How hacking is conceived in social science research

32 min
Math, Functional Programming, Theorem Proving, and an…

32 min
Overview on Current Efforts - We Need Moar H4x0rs?!

34 min
modular and precise resource management
35 min
The future of Neuro-Headsets and concepts towards…

43 min
Fun and games until someone uses IPv6 or TCP
46 min
Engaging social innovation and social innovators

47 min
Trash the prints, print the trash

48 min
How to bring student experiments into space.

49 min
Exploiting Free Data Channels and Security Problems

49 min
How to turn your KVM into a raging key-logging monster

51 min
Guess what? The Government of Rafael Correa actually is…

51 min
An OpenWrt perspective on the development of Linux 802.11…

51 min
Mooltipass, Openpandora/Pyra and Novena/Senoko: how I…
53 min
Amiga Hardware Design And Programming

53 min
Social media break up coordinator

54 min
An introduction to reverse engineering network protocols
55 min
The future of space exploration

55 min
The role of social-graphs for Drones in the War on Terror.
56 min
Cultural Commons durch Kunstraub

56 min
Philosophical Perspectives on Privacy Drawing on the…

57 min
Perceptions of hackers and hacktivists on their…

57 min
From DEFCON to the DARPA Cyber Grand Challenge

57 min
What hacking has to do with avantgarde art of the 1960ies…

58 min
Export controls and exploit regulations: braindead and…

58 min
An inside look at x86 CPU design

58 min
Ein Computerwurm für PLCs

58 min
A brief introduction to search over encrypted data
58 min
Creativity, Archives & Digital Media from the Chinese…
59 min
*(will be specified later based on usability test with…

59 min
A complete toolbox for IoT security

59 min
Large Scale Authorship Attribution from Executable Binaries…

59 min
Understanding and adapting EU legal guidelines from a FOSS…

59 min
Discrimination and ethics in the data-driven society

60 min
phone verified accounts bringing the Hessian army back to…
60 min
The art of failure taught by improv theatre

60 min
An attempt of calculating the economic cost of buffering.

60 min
Calling secret service agents to quit their jobs

60 min
The potential for payment system abuse
60 min
A deep dive into the surveillance features of North Korea's…

60 min
Was kann das? Wie kann ich das nutzen? Wo besteht…

60 min
Disaggregating Data by Race and Ethnicity to Curb…
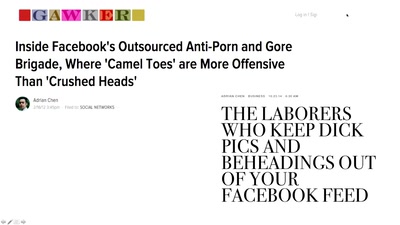
60 min
How social media companies are creating a global morality…
60 min
1 Jahr Freifunk in Südhessen

60 min
Uncovering images from the secret Stasi archives.

60 min
Wie es dazu kam und was daraus zu lernen ist

60 min
How not to do DOCSIS networks
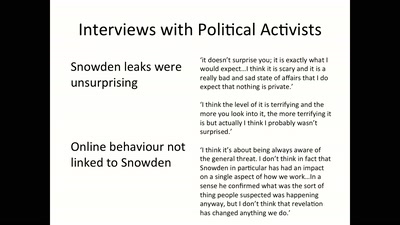
60 min
Findings from a Research Project on Digital Surveillance…

60 min
Or how I learned to stop worrying and love urandom

60 min
Eine Reise auf die dunkle Seite

60 min
Let's Build together a Free, Neutral and Decentralized…
60 min
NDG, BÜPF und wie wir uns dagegen wehren
60 min
Expeditionen ins Kommentierreich

60 min
Geheimdienste kontrolliert man am besten, indem man ihre…
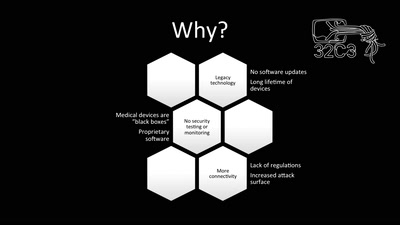
60 min
Living with a vulnerable implanted device

60 min
How advanced threat actors learn and change with innovation…

60 min
Making it easier to avoid low-level compromise, and why…

60 min
from key distribution to position-based cryptography
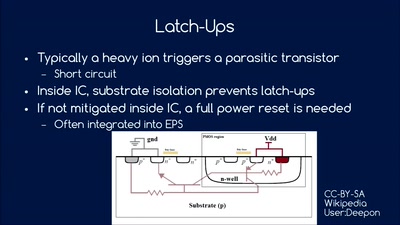
60 min
How hard can it be? An introduction into CubeSat development
60 min
Politische Phrasologie – warum man aus dem ganzen Zeug, das…

60 min
How to design and fabricate soft robots using everyday…

60 min
How to drop more of your privileges to reduce attack…

60 min
A gentle introduction to post-quantum cryptography
61 min
How the institutions fuck up, and how we fuck it up as well

61 min
How drones, IMSI Catchers, and cameras are shaping our…

61 min
The future does not look much brighter than ten years ago.…

61 min
Eine Einführung für blutige Anfänger

61 min
Projektvorstellungen der JunghackerInnen

61 min
An Artificial Intelligence exploration into the creation of…
62 min
Pure capability-based security for UNIX
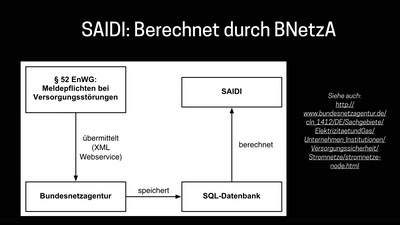
62 min
und warum das gar nicht so einfach ist.
62 min
Access to knowledge for every member of society
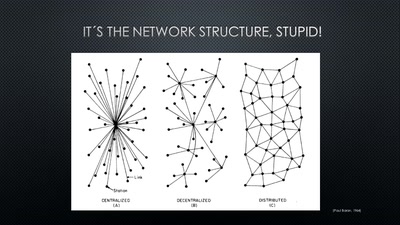
62 min
Conditions for a Successful Market Entry of Decentralized…

62 min
The surveillance state & modern day COINTELPRO tactics

63 min
exploring two decades of transport layer insecurity
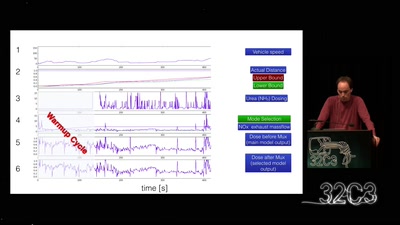
65 min
Take a deep breath into pollution trickery

69 min
Die absurdesten Szenen aus dem…
128 min
Die Wissenschaftsgala vom 32C3