58 min
Physically Unclonable Functions for Hardware Tamper…

62 min
The militarization of the Internet

45 min
The militarization of the Internet
47 min
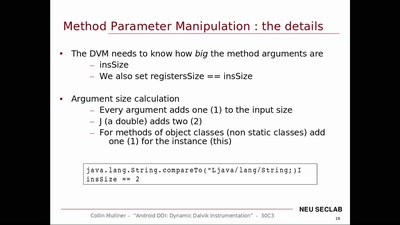
Dynamic Dalvik Instrumentation of Android Applications and…

56 min
what is the winning move?

59 min
Ein Streifzug durch die Fehler in der Kryptografie
58 min
Hacking City-Wide Access Control Systems

59 min
The future of IC analysis
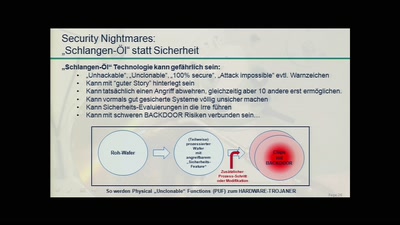
61 min
Von der Historie zur Zukunft

55 min
Attribute Based Credentials in Practice

41 min
Side-Channel (and other) Attacks in Practice
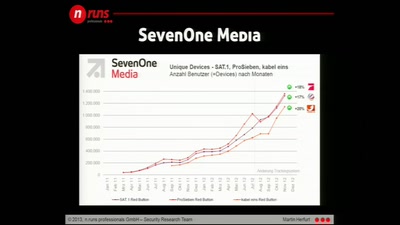
45 min
OMG - my Smart TV got pr0wn3d

47 min
Applying science to eliminate 100% of buffer overflows

51 min
A Decentralized PKI For Social Movements

47 min
Clean boot every boot - rejecting persistence of malicious…

42 min
Embedded Security Using Binary Autotomy

57 min
Was tun nach der mittelmäßigen Kryptographie-Apokalypse?

40 min
Techniques - Tools - Tricks
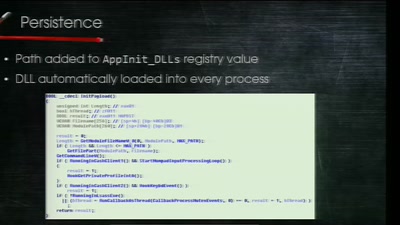
56 min
Stealing Money from ATMs with Malware

45 min
Deep program analysis without the headache